Discover how network forensics helps investigate cyber attacks in real-time. Learn key techniques, tools, and strategies to enhance your cybersecurity defense.
Read MoreDiscover the crucial role of MD5 and SHA1 hash values in digital forensics, and their relevance and reliability in today’s cybersecurity landscape
Read MoreLearn key steps in malware analysis during digital forensics investigations, covering essential techniques and tools for effective forensic analysis.
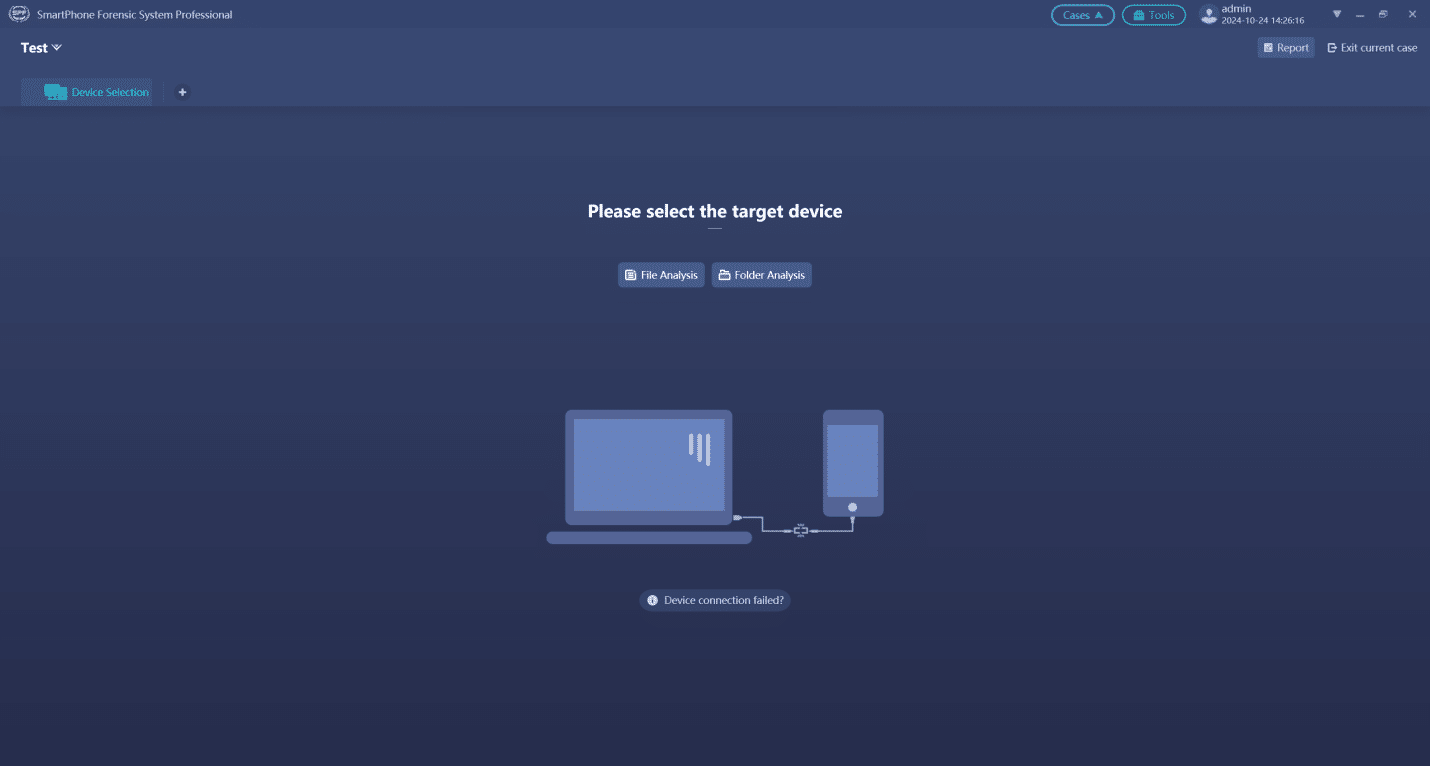
Read MoreThis article is talking about the steps to identify a mobile phone by SPF Pro when disconnected the internet.
Read More