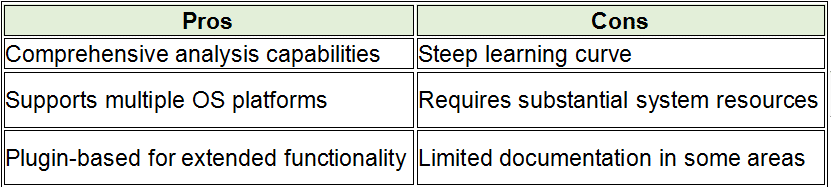
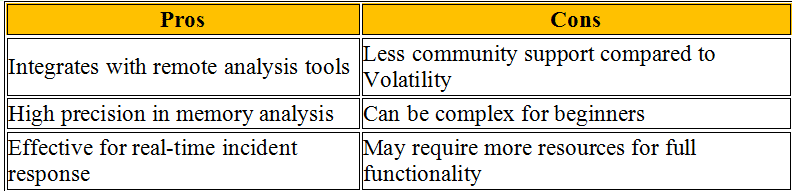
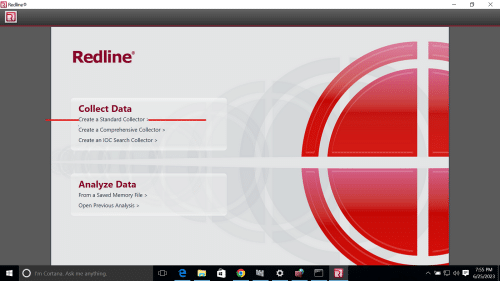
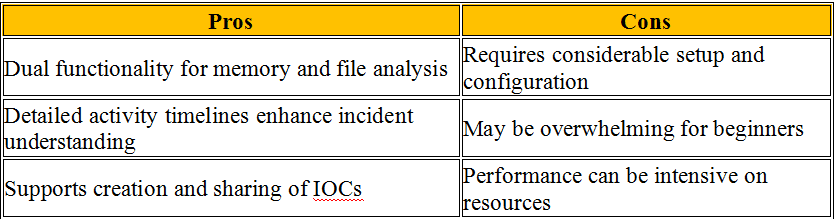
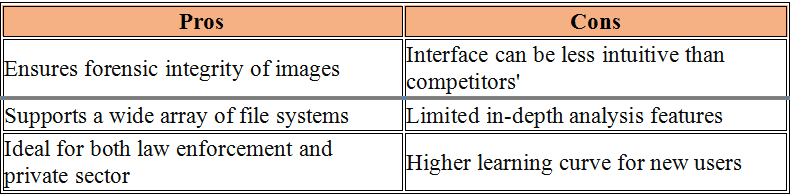
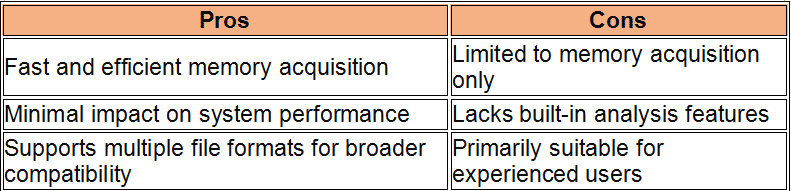
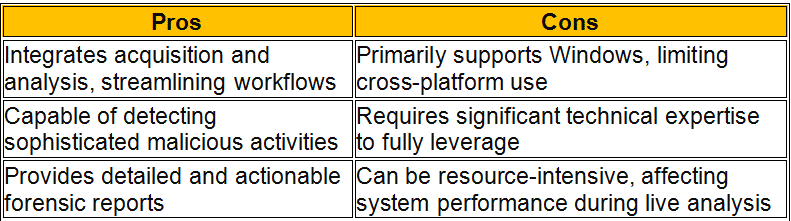
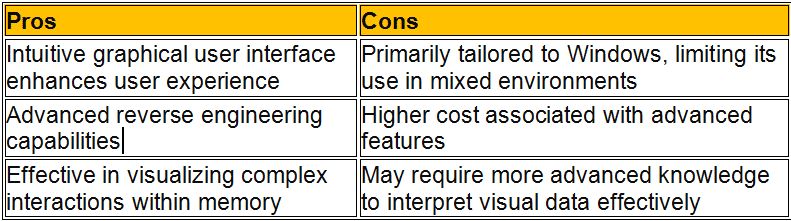
In the realm of cybersecurity, memory forensics stands out as a pivotal technique during incident response operations. This process includes looking at temporary data in a computer’s memory dump to find and understand bad things that happened during an event. Disk forensics looks at data on hard drives. Memory forensics, on the other hand, can analyze data in real time and take snapshots of a system’s memory, which are very important for finding temporary data that would be lost otherwise.
In the following sections, we will delve into the top tools in memory forensics, highlighting how each can be leveraged to fortify incident response strategies effectively. These memory forensics tools and dfir tools, provide comprehensive capabilities ranging from simple memory acquisition to advanced analysis, suitable for various forensic data recovery scenarios.