Phone forensics has become a vital subject in the digital era, fusing technology and law enforcement to find important evidence that often makes or breaks a case. The capacity to retrieve deleted text messages is at the core of phone forensics; this technique not only illuminates private conversations but also yields vital evidence in court cases. The importance of recovering these communications cannot be emphasized, whether it is for the purpose of elucidating the context of discussions or locating timestamps that correspond with significant occurrences. As we go further into the subtleties of phone forensics, knowing these methods empowers professionals and educates the general public about the powerful features and essential role this technology plays in contemporary investigations.
How to Recover Deleted Text Messages in Phone Forensics?

-
Content
- What Is Data Deletion?
- Tools for Recovering Deleted Text Messages
- Step-by-Step Recovery Process
- Case Studies and Tips
- Why Choose SalvationDATA As Your Final Forensic Solutions?
- Conclusion
-
Content
- What Is Data Deletion?
- Tools for Recovering Deleted Text Messages
- Step-by-Step Recovery Process
- Case Studies and Tips
- Why Choose SalvationDATA As Your Final Forensic Solutions?
- Conclusion
What Is Data Deletion?
1. How Text Messages Are Stored on Mobile Devices
- On mobile devices,text messages are saved using intricate systems that differ across the iOS and Android operating systems.
- Text messages are kept on iOS devices in the SMS database of the iOS file system, which is a secure area of the internal memory of the device.
- On the other hand, Android smartphones store these messages using both the internal memory and an extra SIM card.
- Although it may store a limited amount of SMS data, the SIM card mainly stores information on user identity and network parameters.
- Because storage systems vary, forensic analysis methods must be customized based on the operating system.
2. Mechanisms of Deletion
- Physical deleting and mental deletingare the two main ways to get rid of text messages.
- Even if the data is marked as deleted in the device’s file system, the real data stays on the storage media until it is replaced by new data.This method allows for possible rescue because the data is still available in theory.
- On the other hand, actual delete erases all of the data from the device’s memory, making it much harder to get it back.Because of how logical deleting works, messages that have been deleted may still be on the device after following these steps.
- Messages can often be found again using investigative methods, even after the user has deleted them, as long as they haven’t been physically changed.
- Phone forensics experts who want to accurately and quickly get back deleted messages need to know how to do these things.
Tools for Recovering Deleted Text Messages
1. Commercial Forensic Software
- The Cellebrite UFED is a tool that stands out because it can get data back from a lot of different devices.
- For the same reason, Oxygen Forensic Suite is great for getting deeper into mobile data because it has powerful tools for data analysis.
- SPF Prodeveloped by SalvationDATA is another useful tool that can get back lost texts and other digital proof from smartphones.
2. Open Source and Free Tools
- Autopsy has an easy-to-use interface and a flexible design that lets users handle different kinds of digital files.
- Andriller specializes in automating the data extraction and decoding processes, making it particularly efficient for forensic phone analysis.
- The choice between commercial and open source tools should be guided by the specific needs of the investigation, the budget, and the expertise available.
Step-by-Step Recovery Process
1. Preparation
- In phone forensics, the first step is to make sure that everything is well-prepared.
- This means being aware of and following the law, which means getting the right permissions and orders to properly access a gadget.
- Just as important is how the device is handled physically; making sure its purity is kept to avoid any data loss or damage.
- This planning makes it possible for the forensic test to go well.
2. Data Acquisition
When it comes to mobile forensics, there are different ways to get data, based on the gadget and type of data being used. These are the three main ways:
- Physical extraction: To do this, a copy of the whole gadget must be made bit by bit. If the device is open, this is the best way to get back all of your info, even lost files and protected ones.
- Logical extraction: This way gets back data that can be seen by the device’s operating system, like contacts, texts, and photos. It doesn’t get back files that have been removed, though.
- File system extraction: This extraction gives you access to system files and folders. It goes deeper than logical extraction but not as deeply as physical extraction. It works especially well for getting to deleted messages that haven’t been replaced.
3. Data Analysis
- In the last step, forensic tools are used to look through the data that was gathered and find and recover lost text messages.
- During this step, tools like Cellebrite UFED or Oxygen Forensic Suite, which were already stated, are very useful.
- They help not only find the lost messages but also figure out what the results mean so that the restored data is real and complete.
- This careful examination makes sure that the data can be used safely in any legal situation or for more research.
- This organizedway of getting back lost text messages makes sure that each step is done carefully, following legal guidelines and technology standards. This makes the results valid and useful.
Case Studies and Tips
1. Real-World Scenarios
- One notable instance of smartphone forensics involved a corporate espionage case where a senior executive was suspected of leaking sensitive information. Using specialized forensics software, investigators employed data extraction techniques that retrieved deleted messages linking the executive to a competitor. This evidence was crucial in the legal proceedings that followed.
- Another scenario highlighted the importance of mobile forensics tools during a missing person investigation. Forensic experts utilized DFIR tools to analyze the individual’s phone, successfully recovering critical messages that had been hastily deleted. These messages provided leads on the person’s last known interactions and locations, significantly aiding the search efforts.
2. Tips for Ensuring Successful Data Recovery
Several best practices should be followed to get the most out of mobile phone analysis:
- Immediate Action: The faster a device is locked down and analyzedafter data has been deleted, the more likely it is that the data can be recovered. Deleted data can be replaced by new data over time, making it hard to get back.
- Use Comprehensive Tools: Different types of tools should be used for different types of data recovery The best tools are those that can do both mental and physical extractions. This gives you more options for getting data back from different devices.
- Maintain Device Integrity: Make sure that the gadget is always treated in a way that keeps it in its original state. Do not do anything to the gadget that could add new info to its store.
- Document Everything: It is very important to carefully record every step, from the first time the device is handled to the last time the data is recovered. It is important to have this paperwork if the data is to be used as proof in court.
- Stay Updated: The technology landscape, especially concerning mobile devices, is constantly evolving. Keeping up-to-date with the latest in phone forensics near me technologies, tools, and techniques is crucial for ensuring successful recoveries.
Why Choose SalvationDATA As Your Final Forensic Solutions?
1. Pioneering Forensic Innovations
SalvationDATA is at the cutting edge of investigative technology and provides cutting edge solutions that are necessary for current digital investigations. Their tools are the result of more than 20 years of hard work researching and developing them so that they work better when rescuing, analyzing, and protecting digital proof. Contact to apply for a Free Trial now!
2. Customized Solutions for Diverse Needs
SalvationDATA offers custom solutions that meet the needs of all types of customers, including those in the private investigations, law enforcement, and business security fields. Their goods can be used with many different types of devices and systems, from smartphones to cloud storage.
3. Global Trust and Reliability
Trusted by thousands of users across more than 130 countries, SalvationDATA’s tools are known for their reliability and effectiveness in critical investigative scenarios. Their commitment to quality is reflected in their ISO certifications and numerous industry awards.
4. Unmatched Customer Support
SalvationDATA takes pride in its comprehensive customer service, offering 24/7 support, extensive training resources, and regular updates to keep pace with new technological challenges and digital threats.
5. Secure Your Digital World
With SalvationDATA, you gain access to advanced tools that ensure the highest level of data integrity and security. Experience peace of mind knowing that you are using tools that are on the cutting edge of forensic technology.
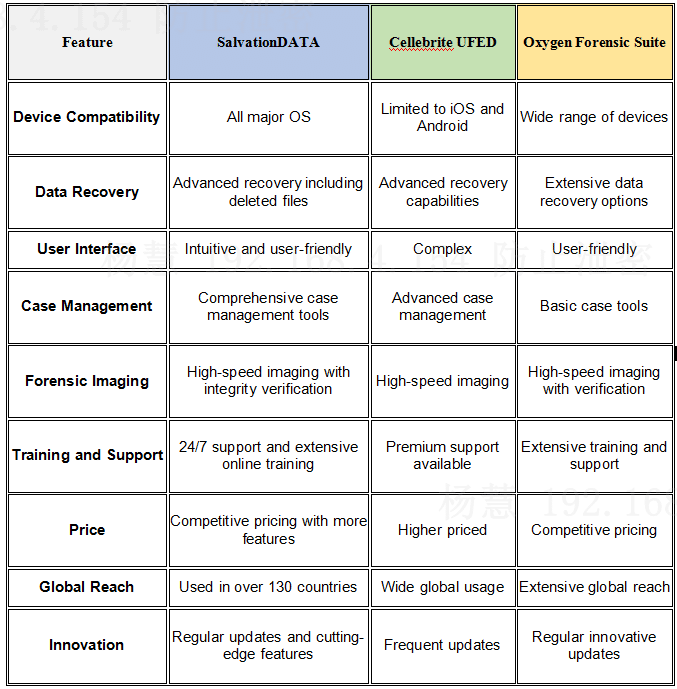
6. Forensic Tools Comparison Table
Conclusion
The field of phone forensics has proven indispensable in both legal and personal contexts, providing key insights through the recovery of deleted text messages. As was shown, a good comeback depends on careful planning, accurate data collection, and careful study of the data. Experts can get back important data that might have been lost by using both paid and free investigative tools to work through the complicated features of modern mobile devices. Real-life case studies also show how important these kinds of investigative techniques are for settling legal issues and helping with important investigations. The techniques and tools that forensic experts use will change along with technology. They have to keep adapting to these changes in order to keep the purity and dependability of their data recovery work.