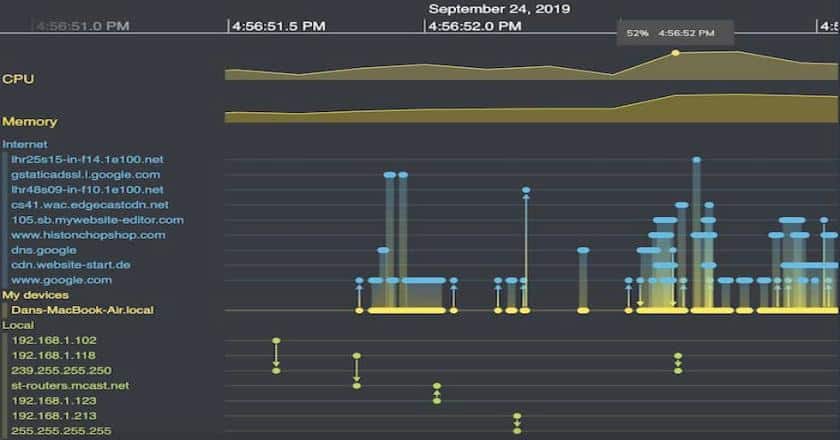
Forensic timeline development has emerged as a crucial tool for deciphering difficult cases in the rapidly changing digital era. Accurately tracking events chronologically is essential for any kind of investigation, including criminal investigations, insider threats, and corporate cyberattacks.
Experts in the area understand that a well-written chronology may be crucial to resolving complex issues, uncovering secrets, and upholding the rule of law.The idea of forensic dates comes from the need to carefully put together digital proof. These timelines show everything that happened, from file access logs to tracking user activity. They help agents find trends, oddities, and possible threats. By leveraging advanced tools and methodologies, forensic experts can piece together even the most fragmented digital evidence.
In order to support experts in their investigation activities, this article delves into tools, procedures, and issues related to creating an accurate forensics timeline for digital evidence.