Digital Forensics and Incident Response (DFIR) is an important part of defense that includes finding cyber dangers, looking into them, and taking steps to stop them. It is very important for keeping private data safe and making sure that IT systems work properly.Due to limited funds and resources, small companies often have trouble putting in place effective DFIR options. Professional tools can be very expensive and you may need to have a lot of special skills to use them. The goal of this guide is to help small businesses set up DFIR options that are both cheap and safe. Businesses can improve their cyber defenses and react to events more quickly by using tools and tactics that don’t cost a lot of money. This piece will talk about a number of low-cost DFIR tools, team-building activities, and best practices that small businesses should follow to keep their computers safe.
Implementing Affordable DFIR Solutions for Cyber Defense

-
Content
- Core Concepts of DFIR
- Affordable DFIR Tools and Resources
- Building a Cost-Effective DFIR Team
- Best Practices for Implementation
- Conclusion
-
Content
- Core Concepts of DFIR
- Affordable DFIR Tools and Resources
- Building a Cost-Effective DFIR Team
- Best Practices for Implementation
- Conclusion
Core Concepts of DFIR
1. Digital Forensics: Recovering and Analyzing Data
A big part of DFIR is digital forensics, which is the study of getting data back from different devices and studying it to find proof of online crimes. This process includes finding systems that have been hacked, getting the data that is needed for legal or criminal reasons, and keeping the data’s security. Businesses can quickly gather and understand digital proof by using special digital tools. Because they can work with a lot of different types of data sources, like computers, phones, and network logs, these tools are very important in the area of digital forensics.
2. Incident Response: Managing and Mitigating Security Incidents
The proactive part of DFIR is incident reaction, which is a set of steps to handle and lessen security mishaps. Usually, the process starts when a security breach is found. Next, it goes through an initial review to figure out how big and bad it is. Once the danger has been found, the next steps are control to stop more damage, elimination to get rid of it for good, and healing to get things back to normal. A clear plan and memory forensics tools that can look at changing data in real time are needed for incident reaction to work well.
3. Challenges and Solutions
Because they don’t have as many resources, small businesses often have trouble putting these core ideas into action. However, if they know what is dfir and how important digital forensics and crisis reaction are, they can be more effective. Using open-source or cheap debugging tools can save you a lot of money while still keeping your data safe. Working with companies that handle computer incidents can also provide specialized help and knowledge when it’s needed.
Businesses can improve their ability to find, react to, and recover from computer events by learning the basic ideas behind DFIR. This cautious method not only keeps important data safe, but it also keeps the business running even when online risks happen. This guide will look at real-world strategies and answers that can help you use effective DFIR practices, even if you don’t have a lot of money.
Affordable DFIR Tools and Resources
1. Free and Low-Cost Tools
You shouldn’t have to worry about money if you want to use good choices for dfir (Digital Forensics and Incident Response). You can use a lot of free and low-cost tools to make your small business safer online.
2. Open-source EDR Tools
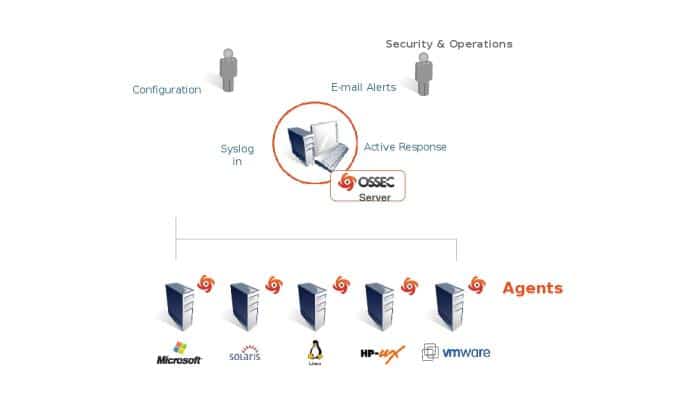
- OSSEC: OSSEC is an open-source endpoint detection and response (EDR) tool that can watch and send alerts on a wide range of endpoints. It helps find bad behavior and policy violations across many platforms, which makes it an important tool for any dfir. Contact to get a Free Trial now!
- Wazuh: Wazuh is a powerful open-source EDR tool that can be used for security tracking, log data analysis, and attack discovery. It works with a lot of different settings and can find and stop threats in real time.
3. Forensic Analysis Software
- Autopsy: Autopsy is a free, open-source digital forensics platform that simplifies the process of investigating cyber incidents. It supports various file formats and offers modules for timeline analysis, keyword search, and image analysis. It’s a vital tool for understanding what is digital forensics in cyber security.
- VIP 2.0: VIP 2.0 is a cost-effective forensic analysis tool from SalvationDATA, key features including the ability to recover lost data, cut up files, and make detailed reports. It has an easy-to-use interface that lets people with little experience with digital forensics do it.
4. Cloud-Based Solutions
Leveraging cloud-based solutions can significantly reduce costs while enhancing the capabilities of digital forensics and incident response efforts. Cloud resources offer scalable, on-demand access to powerful tools and services, eliminating the need for expensive on-premises infrastructure.
- AWS CloudTrail: AWS CloudTrail is a service in the cloud that lets companies keep track of, log, and log account activity linked to steps taken in their AWS infrastructure. In a real sense, it helps answer questions like “what is dfir?” by giving useful information for investigative research and event reaction. Click to get a Forensic Download here!
- Microsoft Azure Security Center: This all-in-one security control system protects against advanced threats across mixed cloud services. It works well with other Azure services and lets you see all security events in one place, which speeds up the response time to incidents.
5. Utilizing Free and Low-Cost Resources
There are many free tools that small businesses can use to improve their digital skills. Online groups like open-source communities, lectures, and boards can help you learn and get help. A lot of cyber incident response companies also offer free tools and resources to help businesses improve their security.
6. Implementing DFIR Best Practices
Adding low-cost tools and cloud-based solutions to your defense plan can make it much easier to find cyberattacks, react to them, and recover from them. Businesses can make smart choices that fit their budget and protection needs when they know all of their options. This method makes sure that even small businesses can keep their protection strong without spending a lot of money.
Building a Cost-Effective DFIR Team
1. Team Structure: Essential Roles and Responsibilities
Thinking carefully about what each member of a cost-effective digital forensics and incident response team should do is important to make sure that all the tasks are done. On a well-organized team, the following critical roles are common:
- Incident Response Manager: Oversees the whole incident reaction process, works with other team members to make sure steps are taken quickly and correctly during a cyber attack.
- Digital Forensics Analyst: Its main goal is to gather, store, and analyze digital proof. This part is very important for figuring out what kind of attack it is and who the danger players are.
- Security Analyst: Keeps an eye on networks and systems for any strange activity, looks over security reports, and handles the first round of possible events.
- System Administrator: Makes sure that IT systems are set up and maintained correctly, including installing changes and putting in place security measures to stop future problems.
- Legal Advisor: Helps people understand the rules and laws that apply to data breaches and how to handle digital proof.
2. Training and Certification: Affordable Options
It doesn’t have to cost a lot to give your defense team the skills and information they need. There are a number of low-cost training and licensing choices that can help team members stay up to date on the latest trends in digital forensics and crisis response.
- SANS Cyber Aces Online: This free online course covers basic cybersecurity topics that are important for digital analysis and event reaction. It’s a great place to start for team members who are new to the field.
- Cybrary: Cybrary has many free and low-cost classes on a wide range of hacking themes, such as dfir. Their classes are put together by experts in the field and cover both the theory and practice of it.
- CompTIA Security+ Certification: This well-known certification covers important hacking skills, such as how to handle incidents and do analysis. It’s an affordable choice that gives you a strong basis for what digital forensics is in cyber security.
- Practical Experience: Inviting team members to take part in hacking events and hands-on labs can help them gain useful real-world experience without spending a lot of money. A lot of websites let you use virtual settings for free so you can work on your DF skills.
Small businesses can build a cost-effective defense team that can handle and lessen online risks by carefully choosing jobs and offering low-cost training. This strategy method makes sure that businesses can keep their cybersecurity strong even if they don’t have a lot of money to spend on it and act quickly to events.
Best Practices for Implementation
1. Basic Cybersecurity Measures: Implementing Fundamental Security Practices
For dfir (Digital Forensics and Incident Response) to work, basic protection steps must be put in place. Regular changes and fixes are one of the most important things to do. By keeping systems and software up to date, you protect yourself from known flaws that hackers could use. Patching your systems on a regular basis is a simple but effective way to make your business safer.
Training and making employees aware of things are both very important. Cybersecurity risks often target people, so it’s important for workers to be able to spot and deal with possible threats. Staff can learn about phishing scams, social engineering, and other common tricks hackers use in regular training meetings. A well-informed team is an important part of a good defense plan because it lowers the chance of mistakes happening because of human error.
2. Continuous Improvement: Regular Assessment and Updating of DFIR Strategies
Continuous growth is necessary to keep a strong dfir framework. Your defense tactics should be reviewed and updated on a regular basis to make sure they continue to work against new threats. Reviewing and simulating your incident reaction plan on a regular basis can help you find holes in it and make changes quickly.
Developing a comprehensive dfir report after each incident is a best practice. This report should document the incident’s details, the response actions taken, and the lessons learned. Analyzing these reports can provide valuable insights into dfir meaning and highlight areas for improvement.
Businesses can build a strong defense against cyberattacks by combining basic security measures with a dedication to always getting better. This method not only makes it easier to handle events, but it also improves general safety, protecting against online risks for a long time.
Conclusion
Finally, if you want to keep your business safe from online dangers, you need to have a good dfir (Digital Forensics and Incident Response) plan in place. Small businesses can get around budget problems and improve their safety by learning what dfir means and using low-cost tools and resources. Your company will be ready to handle and lessen events if you put together a cost-effective defibrillation team with the right roles and low-cost training choices.
Best practices, like regular updates and fixes, training for employees, and ongoing evaluation of defense tactics, make your security even stronger. Making thorough DFIR reports after events gives useful information and encourages ongoing growth.
Businesses can put in place strong, cost-effective dfir solutions that protect their digital assets by following the advice in this piece. Stay alert, keep learning, and keep improving your defense practices to stay ahead of online dangers and make sure your long-term strength.