Today’s fast-paced and digitally connected world makes it necessary to protect business info. It’s also an important part of being honest as a business. Today, it’s more important than ever to take strong steps to keep your information safe. Database encryption is one of the most important parts of protecting against data leaks. Data stays safe, whether it’s at rest or in motion, because encryption changes private data into forms that can’t be read by people who aren’t supposed to.This article explores the five major database encryption technologies that every enterprise should know to enhance its security posture, as well as the scenarios in which they are most suitable, providing a roadmap for enterprises to effectively strengthen data security measures.
Top 5 Database Encryption Techniques for Businesses

-
Content
- Why Database Encryption is Crucial?
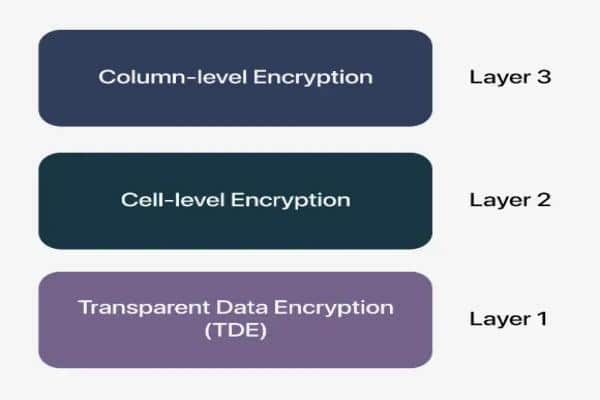
- Technique 1: Transparent Data Encryption (TDE)
- Technique 2: Column-Level Encryption
- Technique 3: Application-Level Encryption
- Technique 4: Disk Encryption
- Technique 5: End-to-End Encryption
- How to Choose the Right Encryption Technique?
- Conclusion
-
Content
- Why Database Encryption is Crucial?
- Technique 1: Transparent Data Encryption (TDE)
- Technique 2: Column-Level Encryption
- Technique 3: Application-Level Encryption
- Technique 4: Disk Encryption
- Technique 5: End-to-End Encryption
- How to Choose the Right Encryption Technique?
- Conclusion
Why Database Encryption is Crucial?
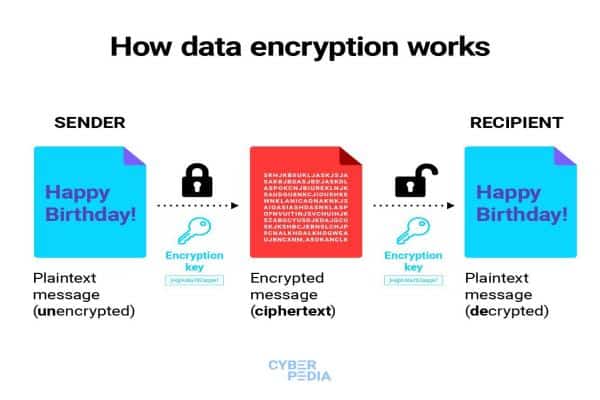
1. How Database Encryption Works
- Database encryption converts data that can be read into an unreadable format that can only be accessed with the right decryption key.
- This guarantees that sensitive information cannot be interpreted by unauthorized persons even if they manage to get access to the database.
- Data protection techniques that are widely used to safeguard data both in transit and at rest include sql database encryption and database encryption solutions.
2. Key Benefits
- The main benefit of database encryption is that it keeps private data safe from hackers, which lowers the chance of being seen after a security breach.
- Encryption also helps companies follow rules and standards in their industry, such as GDPR and HIPAA.
- Compliance is important not only to stay out of trouble with the law, but also to keep the trust of customers who want their personal information to be kept safe.
With database security options, companies can improve their protection and make customers feel more confident in them.
Technique 1: Transparent Data Encryption (TDE)
1. What is TDE and How It Encrypts Data at Rest?
A common way to secure data is with Transparent Data Encryption (TDE), which locks the whole database file and saves data that is not being used. TDE is different from other encryption methods because it works at the database level. Because of this, it is a good choice for businesses that want to use encryption with little trouble.
2. Use Cases and Advantages
- TDE is especially helpful for companies that need security options that work with their existing apps without having to change them.
- It’s often used to keep private customer data safe in fields with strict security standards, like finance and healthcare.
- The good thing about it is that applications don’t have to change anything about database searches or logic during the encryption process.
3. Limitations
- One big problem is that it can’t protect data while it’s being used, so any private data that’s being handled in memory is still open to attack.
- In addition, TDE may slow things down a bit, especially with bigger systems.
Technique 2: Column-Level Encryption
Column-level encryption is a focused method that only protects certain entries in a database, not the whole database. This method gives you more precise control over what data is secured. This method is often chosen because it can be used in a variety of ways and is very accurate when protecting sensitive data.
1. Use Cases Where Column-Level Encryption is Beneficial
- This type of encryption is highly beneficial in industries like finance and healthcare, where personal and financial data must be protected.
- Database security becomes a priority when dealing with sensitive records, and column-level encryption allows businesses to safeguard essential information without unnecessarily encrypting less sensitive data.
- It is particularly useful in database forensics, where only specific data fields need protection during investigations.
2. Pros
- Controlling the spread of encryption is one of the best things about column-level encryption.
- Businesses can only secure the most important parts of data, which improves speed and reduces the amount of space needed.
3. Cons
- But handling database encryption solutions and making sure that encryption rules are the same across all fields can make mistakes more likely, which will make the system harder to keep up over time.
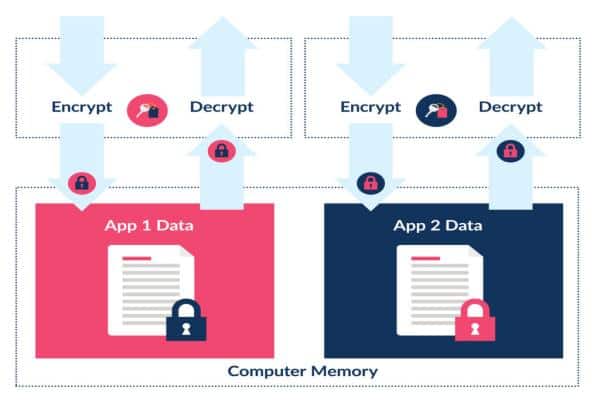
Technique 3: Application-Level Encryption
1. How Encryption is Managed at the Application Layer
- Application-level encryption adds an extra layer of protection by encrypting data before it even gets to the database.
- This makes sure that private data, like financial or personal information, is protected at the application level, so that people who aren’t supposed to can’t read it, even before it gets to the database.
- Businesses that want to keep full control over security will find this way very useful.
2. Pros
- The primary benefit of application-level encryption is that it offers robust security, as sensitive information is encrypted before it enters the database.
- This approach can help businesses protect against database attacks and ensure that their critical information remains safe.
- Additionally, by handling encryption at the application level, businesses can control and manage encryption policies more effectively.
3. Cons
- It becomes essential to maintain encryption keys properly as any breach in this area might result in serious security flaws.
- Furthermore, since data must be encrypted and decrypted numerous times when using application-level encryption, longer processing times may occur.
Technique 4: Disk Encryption
1. Full Disk Encryption as It Relates to Database Security
To ensure that all data saved on the disk is safe, full disk encryption (FDE) encrypts the whole disk that houses the database. In the event that the disk or database server is taken, this method blocks unauthorized access to the data, making it a potent defensive mechanism for physical security. Sensitive data is protected from reading until the right decryption key is supplied thanks to disk encryption.
2. Use Cases and Scenarios Where Disk Encryption is Effective
- It is best to use disk encryption in places where physical theft is a big problem. This method can keep private information safe even if the hardware is broken, like when movable devices or faraway platforms are involved.
- Also, disk encryption makes SQL database recovery safer by lowering the chance that someone will get in without permission during the recovery process.
3. Considerations
- Disk encryption protects against physical threats, but it doesn’t protect data that is being used or stop threats from internally.
- Furthermore, it is important to know that full disk encryption only works when the computer is turned off; when the computer is on, approved users can still access protected data, which could be dangerous if there are bad people inside the company.
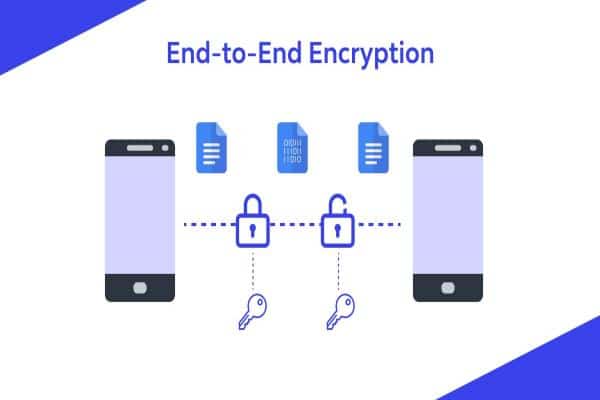
Technique 5: End-to-End Encryption
1. End-to-End Encryption and Its Application in Database Security
It is very hard to read or change data from the time it is created until it is sent or saved. This is called end-to-end encryption (E2EE). E2EE makes sure that data is safe while it is being saved in the database and while it is being sent between people and systems.
2. How It Ensures Data Is Encrypted Throughout Its Lifecycle
- End-to-end encryption is particularly effective because it encrypts data at the source and keeps it encrypted until it reaches the intended recipient, ensuring no third parties can intercept or tamper with the data.
- This method offers superior protection, even against sophisticated database attacksthat might target data at various points in its journey.
3. Pros
- Highest level of security is the main benefit of end-to-end encryption.
- This makes it perfect for companies that deal with very private data, like healthcare or financial institutions.
4. Cons
- However, this encryption method is hard to set up and manage because it is so complicated.
- It’s important to keep track of keys carefully, and it can slow down speed, especially when working with big datasets.
How to Choose the Right Encryption Technique?
1. Factors toConsider
Businesses have to think about a lot of things when choosing the right database encryption method. These include how sensitive the data is, how fast the system needs to be, and how to make sure it meets legal standards. When it comes to very private data, end-to-end encryption or application-level encryption provide the best level of security. But these ways can make things more complicated and slow things down, especially for systems that are very big.
2. Scenario-Based Recommendations
For businesses handling confidential financial information, sql database encryption or disk encryption may be ideal solutions to ensure the protection of data at rest. Understanding which database encryption method can you use to encrypt data at rest? can be crucial for businesses focused on securing stored data while avoiding performance bottlenecks. Additionally, in cases where real-time data protection is necessary, techniques like application-level encryption can offer enhanced security throughout the data’s lifecycle.
3. Employee Training and Awareness
Training employees is another important part of a good security plan. By accident, even the most powerful security methods can be broken.Training workers on a regular basis can help them spot possible risks, understand why proper encryption is important, and stay up to date on the newest database security solutions. This not only lowers the chance of an internal breach, but it also makes the company safer generally.
Conclusion
Nowadays, everything is based on data, so keeping private data safe is very important. Encrypting databases is still one of the best ways to do this. By using the right encryption methods, like end-to-end encryption, column-level encryption, and sql database encryption, businesses can keep their data safe and follow rules like GDPR and HIPAA.
In the end, using best practices for database encryption solutions will not only keep private information safe, but it will also help build trust with partners and users. By staying informed and taking action, businesses can make sure their data is always safe in a secure environment.