Explore 2025’s digital forensics certifications, industry trends, and high-demand roles like Forensic Analyst and Cloud Investigator, with insights into compliance and career advancement strategies
Unveil 2025 digital forensics trends on salvationdata.com. See how AI, ML & cloud reshape it, impacting crime probes & data security.
Cybersecurity and digital forensics partner to stop cybercrime: prevent attacks, investigate breaches. Explore their role in fighting ransomware, securing evidence, and tools like SalvationData’s solutions that bridge defense and justice.
Learn how to recover deleted files using expert tools and methods. A professional guide to efficient file recovery in digital forensics and more.
Axon Evidence offers secure, cloud-based digital evidence management with advanced tools, ensuring compliance and efficiency for law enforcement agencies.
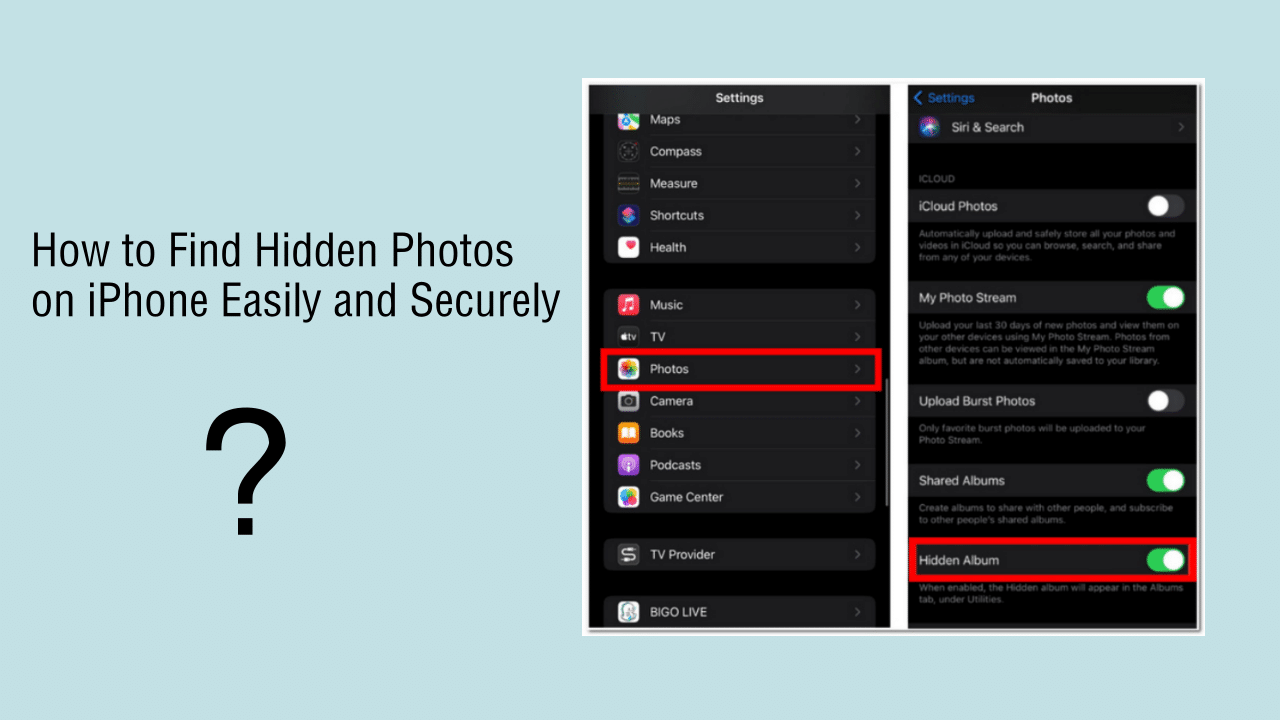
Discover how to find hidden photos on iPhone with professional methods. Learn tips, tools, and techniques to uncover hidden images securely.
Discover the best tools and techniques to recover recently deleted messages on iPhone and Android. Learn step-by-step methods for efficient recovery.
This article is exploring the top 10 digital forensics software. Cutting-edge tools to extract and analyze critical data at your fingertips.
Discover the leading data loss prevention solutions to protect your business in 2025, ensuring comprehensive security and compliance.
Learn how to use Hashcat effectively for password recovery. A step-by-step guide for professionals in digital forensics and cybersecurity.
Explore how logical evidence strengthens digital forensics by providing accurate, reliable insights to solve cases and support investigations.
Discover the top skills needed to excel as a forensic analyst in 2025, including digital forensics, cybersecurity expertise, and more.