Leveraging Intelligence Solutions for Digital Forensics Success

-
Content
- Introduction
- Intelligence Integration in Digital Forensics
- Tools and Practices for Digital Forensics
- Digital Forensics Process
- Conclusion
-
Content
- Introduction
- Intelligence Integration in Digital Forensics
- Tools and Practices for Digital Forensics
- Digital Forensics Process
- Conclusion
Introduction
In the evolving landscape of digital forensics, intelligence solutions stand at the forefront, offering groundbreaking approaches to combat and analyze cyber threats. These solutions harness the power of advanced analytics, machine learning, and big data technologies to provide comprehensive insights into digital evidence. Modern intelligent methods in digital forensics include the integration of cyber threat intelligence solutions and digital intelligence solutions, enhancing the capabilities of investigators to preemptively identify, assess, and mitigate cyber threats. By leveraging digital forensic tools and methodologies, professionals can uncover intricate details from digital artifacts, offering a clearer understanding of cyber incidents and ensuring a robust security posture. This fusion of technology and expertise marks a significant leap towards a more proactive and informed approach in the realm of digital forensics.
Intelligence Integration in Digital Forensics
The integration of intelligence solutions into digital forensics marks a paradigm shift in how investigations are conducted, offering a more nuanced and efficient approach to solving cyber crimes.
1. Automated Analysis
Digital forensics has made great progress in the field of intelligence solutions. The most recent advancements in AI and machine learning enable this technology to handle and analyze enormous datasets autonomously—a feat that would be impossible for human analysts to do on their own. This increases the speed at which relevant information is found and improves the quality of the data produced. This frees up digital forensic analysts from the tedious work of organizing data, allowing them to focus on the strategic interpretation and in-depth examination of data. This change improves the pace of the investigation while maintaining the caliber of the insights gained, resulting in better decision-making and strategic planning for cyber security initiatives.
2. Invaluable in Identifying Crime
The detection and investigation of cybercrime depend heavily on intelligence solutions. Cybercrime investigators are now better able to anticipate and identify harmful activity since they are equipped with cutting-edge cyber threat intelligence technologies. Proactive threat hunting depends on this predictive capacity to prevent prospective intrusions before they happen. The discipline of digital forensics has grown more dynamic by using such knowledge, moving from reactive post-incident analysis to proactive crime prevention and strategic threat intelligence.
3. Pattern Recognition and Anomaly Detection
Digital forensics has changed significantly as a result of sophisticated algorithms’ capacity to identify patterns and abnormalities. In addition to recognizing existing threats, pattern recognition and anomaly detection help anticipate and be ready for new kinds of cyber attacks. Because of this, digital forensic tools that have these features are not only tools for investigation; they are also tools for prediction, providing information about potential hazards in the future. Due to its ability to enable the creation of preventive actions against future cyber criminal activities and secure digital assets in an ever-changing threat environment, this dual function is essential for a strong cyber threats and security
By harnessing these capabilities, intelligence solutions significantly enhance the efficacy and scope of digital forensics. They not only facilitate a deeper understanding of cybercrime but also bolster the security frameworks within which digital forensics operates, setting a new standard in the quest for digital justice and protection.
Tools and Practices for Digital Forensics
In the evolving landscape of intelligence solutions, a closer look reveals the crucial role of data intelligence solutions in enhancing digital forensics. These solutions, when integrated with dfir tools and the establishment of a digital forensic lab, significantly amplify the capabilities of forensic analysts. The digital forensics analyst operates at the heart of this process, employing a variety of tools, including ediscovery tools, to navigate through complex data landscapes. These technologies and practices not only streamline the investigative process but also ensure a higher degree of accuracy and reliability in digital evidence analysis.
Tools Used in Intelligence Solutions
1. Computer Forensics – ProDiscover Forensic
ProDiscover Forensic emerges as an indispensable asset in the arsenal of computer forensics. This sophisticated tool extends its utility beyond mere data retrieval, offering a suite of features that cater to a comprehensive digital investigation. The ability to perform disk imaging allows for the creation of exact clones of storage devices, ensuring that evidence remains untampered. The file recovery function delves deep into systems to reclaim data that may have been intentionally concealed or deleted. Moreover, ProDiscover Forensic’s data analysis capabilities are not confined to surface-level information it can analyze file structures and system metadata, revealing a narrative hidden within the binary code. The software’s robustness lies in its user-friendly interface coupled with powerful under-the-hood analytics, making it a preferred choice for forensic experts dedicated to preserving the integrity of the digital investigation process. Whether it’s for corporate audits, legal investigations, or compliance checks, ProDiscover Forensic stands as a bulwark, ensuring that digital evidence is meticulously analyzed and secured for any scrutiny it may face. Contact to apply for a Free Trial now!
2. Mobile Forensics – Magnet GRAYKEY
Due to Magnet Graykey’s remarkable capacity to unlock and retrieve data from mobile devices, it has emerged as a key component in the field of mobile forensics. In order to recover data that is often essential for legal and security reasons, this program digs underneath the surface of encrypted and password-protected devices. A device’s use and user behavior may be fully understood by examining the plethora of information that its advanced technology can uncover, ranging from call records and texts to app data and GPS history. Magnet GRAYKEY is an analytical wizard that is an invaluable asset to current law enforcement and intelligence services, especially in situations of digital malfeasance or criminal investigations. Pushing the limits of what’s feasible in terms of data extraction and analysis from personal devices, it serves as a monument to the developments in digital forensic technologies.
3. Video Forensics – VIP 2.0
VIP 2.0‘s cutting-edge features are completely changing the video forensics industry. This program is quite helpful for properly understanding events since it can do much more than just frame-by-frame analysis and quality improvement. It can also use noise reduction methods, stabilize unstable footage, and dramatically upgrade video resolution. VIP 2.0’s technology makes it possible to see minute details that are often invisible to the unaided eye, such minute items moving across a scene or minor backdrop changes. These improvements are not only important from a technological standpoint, but they also play a crucial role in court cases where video evidence may make all the difference. From SalvationDATA, VIP 2.0 has grown to be an indispensable tool for forensic specialists who build a true timeline of events using the clarity and integrity of video evidence.
4. Database Forensics – FTK (Forensic Toolkit)
FTK (Forensic Toolkit) stands as a vanguard in database forensics, offering a robust suite for in-depth analysis and recovery of digital evidence. Its comprehensive capabilities extend to advanced data carving techniques, which meticulously sift through unstructured data to reconstruct valuable pieces of information. With its potent encryption analysis, FTK can penetrate protective layers to access and interpret secured data, a vital function in a landscape where encryption is ubiquitous. Timeline generation is another key feature, synthesizing events into a coherent chronology, thus proving indispensable for unraveling the complexities of sophisticated data breaches. This tool embodies the convergence of thoroughness and precision, making it an essential element for professionals dealing with the intricacies of database forensics and the examination of digital artifacts. Click here to Update your software!
Practical Applications
1. Cybercrime Investigation: Digital forensic tools are pivotal in investigating various forms of cybercrime, from data breaches to online fraud. They enable the identification of attack vectors, the recovery of stolen data, and the tracing of cyber criminal activities.
2. Legal Evidence Gathering: In legal contexts, these tools are used to collect and preserve digital evidence for court proceedings, ensuring that the evidence is admissible and has been handled according to legal standards.
3. Security Breach Analysis: Following a security breach, forensic tools help organizations analyze how the breach occurred, assess the extent of the damage, and implement measures to prevent future incidents.
Real-world Examples
1. ProDiscover Forensic in Corporate Espionage: A major corporation utilized ProDiscover Forensic to investigate an internal case of corporate espionage, successfully identifying the perpetrator by recovering deleted files and emails from the suspect’s computer.
2. Magnet GRAYKEY in Missing Person Case: Law enforcement agencies used Magnet GRAYKEY to unlock the smartphone of a missing person, uncovering critical communications that led to the individual’s location and the arrest of the kidnapper.
3. VIP 2.0 in Traffic Incident Analysis: In a disputed traffic incident, VIP 2.0 was employed to enhance surveillance footage, clearly revealing the sequence of events and contributing to the resolution of the case.
This detailed exploration highlights the integral role of digital forensic tools within the broader spectrum of intelligence solutions, showcasing their capabilities, applications, and the tangible impact they have in the real world. By leveraging these advanced tools, professionals in digital forensics are better equipped to tackle the challenges posed by cybercrime, ensuring the safety and security of digital spaces.
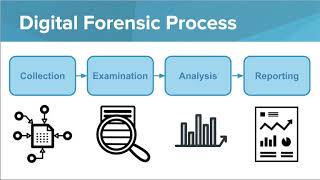
Digital Forensics Process
The practice of digital forensics involves a series of rigorous stages that are specifically intended to guarantee the accuracy and dependability of the evidence that has been acquired. The first step is the identification of prospective evidence, in which experts locate information pertinent to the inquiry. Preservation then takes precedence, making sure that data is correctly duplicated and protected from modification. The analysis step is a thorough examination of the material using digital forensic techniques to find concealed information and establish the truth. Following a thorough recording of findings, procedures, and results, Presentation is the last stage in which the evidence is gathered and presented in a way that is understandable to non-experts, as in a court of law.
By creating a proactive defensive system, incident response’s effectiveness is increased when forensics is integrated with it. This synergy enables teams to move quickly from the stages of comprehensive forensic investigation and analysis to the immediate containment and mitigation of dangers as recognized by cyber threats and security regulations. It guarantees that digital evidence is used not just for research subsequent to the occurrence but also enhances the cybercrime investigator’s understanding of averting such situations in the future.
The significance of an organized digital forensics process and its connection with incident response tactics are emphasized in this succinct but thorough synopsis, which also highlights the development of intelligence solutions in protecting digital environments from the constantly changing threat landscape.
Conclusion
Our exploration of the crucial role intelligence solutions play in contemporary digital forensics has resulted in this essay, which also emphasizes the significance of cutting-edge technologies, the integration of forensics and incident response, and the methodical procedures that digital investigations need. Professionals may handle cyber risks with accuracy by using specialized tools such as Magnet GRAYKEY, VIP 2.0, FTK, ProDiscover Forensic, and others. These tools are made effective by using real-world examples and actual implementations. Digital forensics processes are made more secure and reliable by the smooth integration of these instruments, which provide a strong defense against cybercrime.