A Complete Guide for Database Analysis: 5 STEPS

Overview
In recent years, with the frequent occurrence of online gambling and online fraud cases, database forensics is becoming more and more important. Because a large amount of evidence is stored in the database, thus the database analysis & database forensics plays a vital role in helping investigators to quickly extract accurate data involved in the case (such as: members who participate in online gambling , profit table, personnel organization structure table, network platform capital flow table, etc.), and accurately crack down on Internet crimes.
Steps for Database Analysis in a Case
There is an existing website database (MySQL database data file) involved in the case, which needs to be analyzed according to the following requirements to obtain relevant data:
Inspection Material: data.7z
Analysis Tool: DBF Database Forensic Analysis System
Step 1. Unzip the inspection material file and obtain the MySQL database file “data”.
Step 2. Find information about the suspect named Aaron
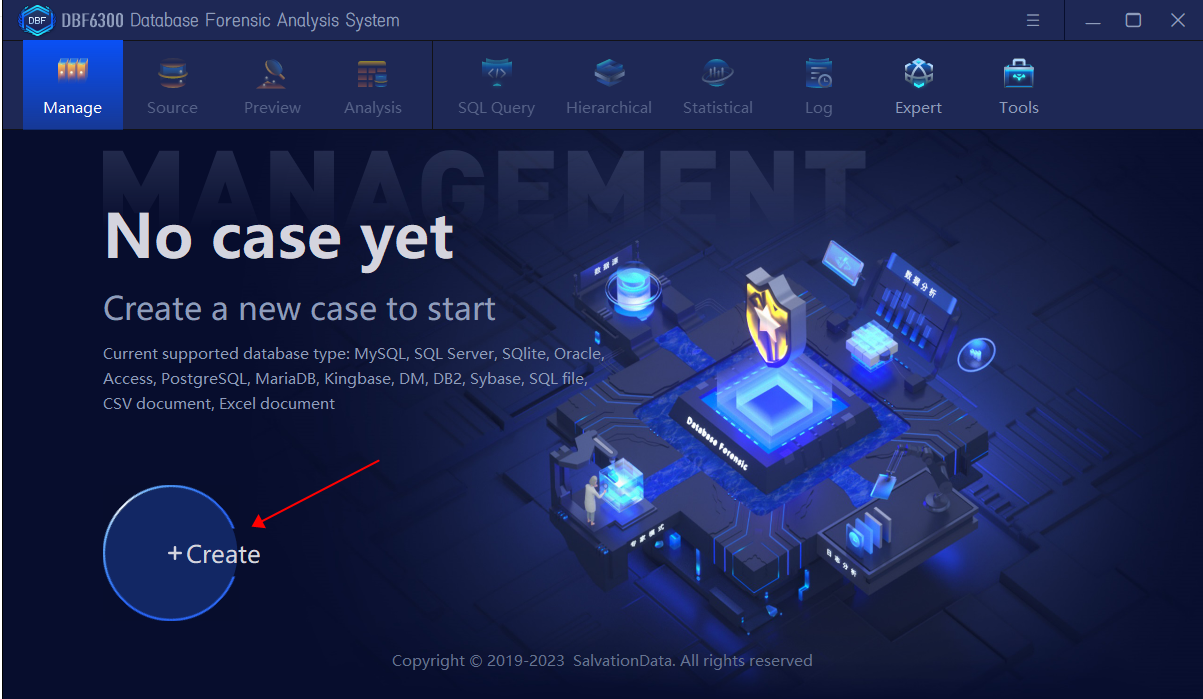
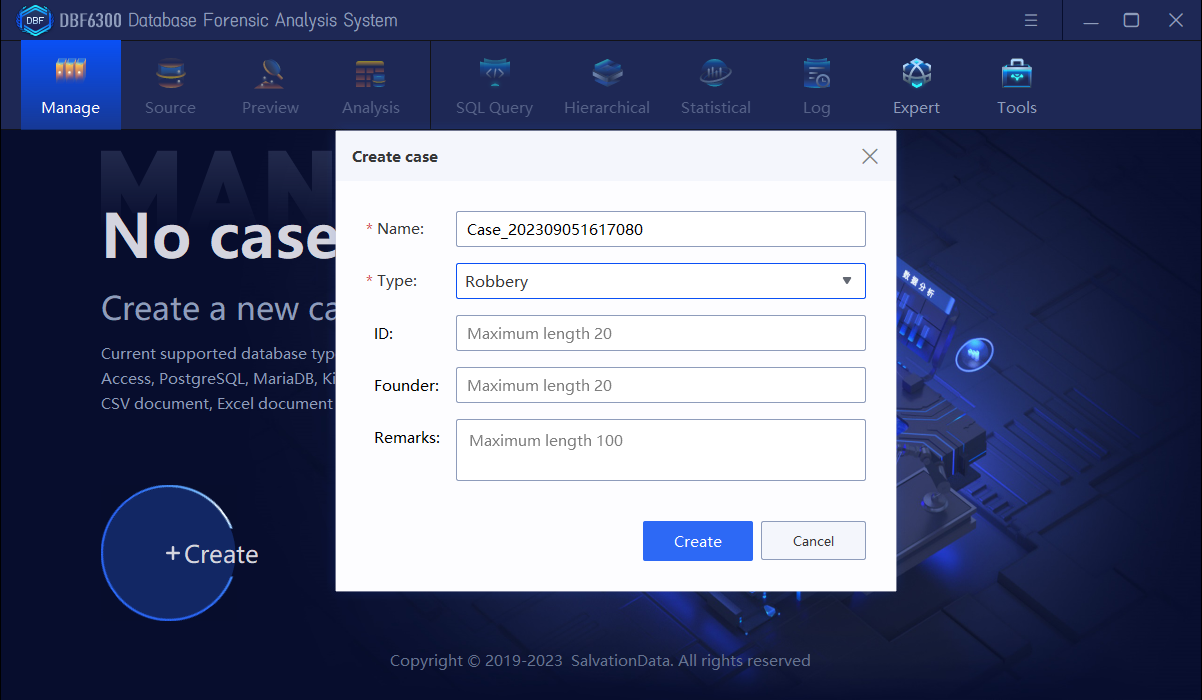
1.Open the DBF6300 Database Forensic Analysis System, click “Create” to create a new case and then input the basic case information.
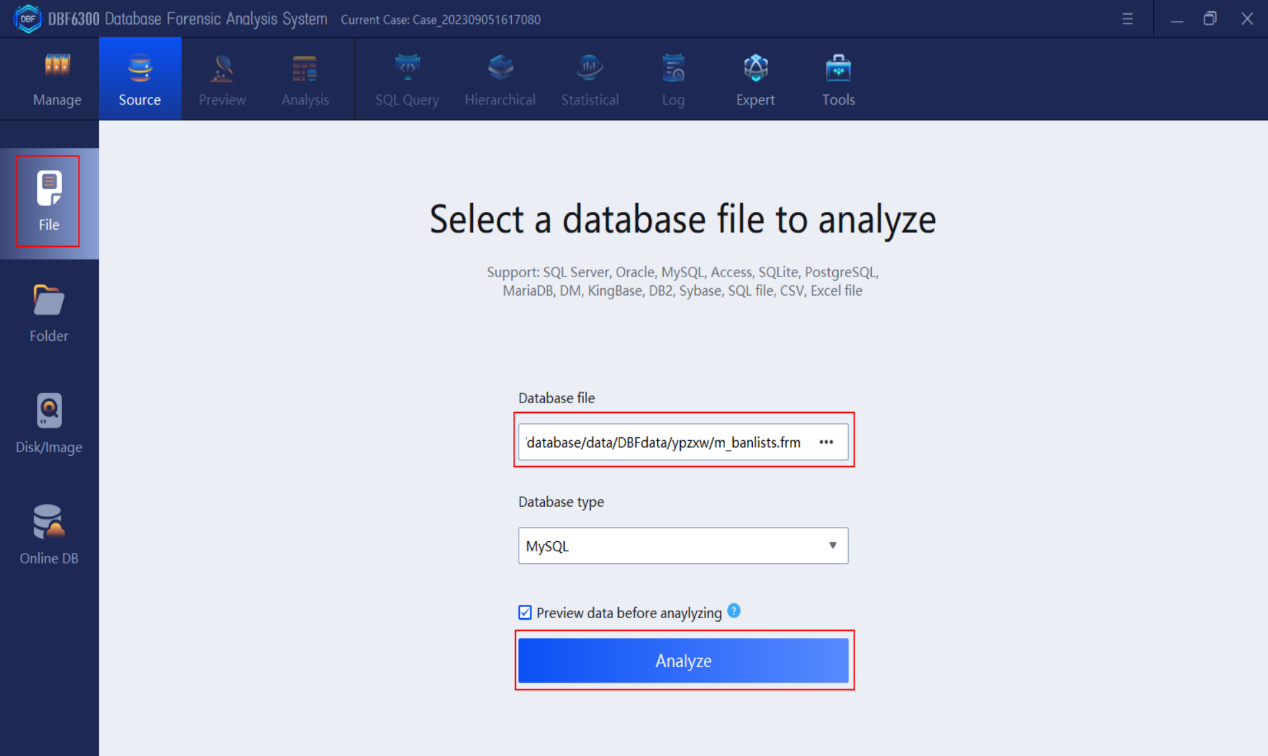
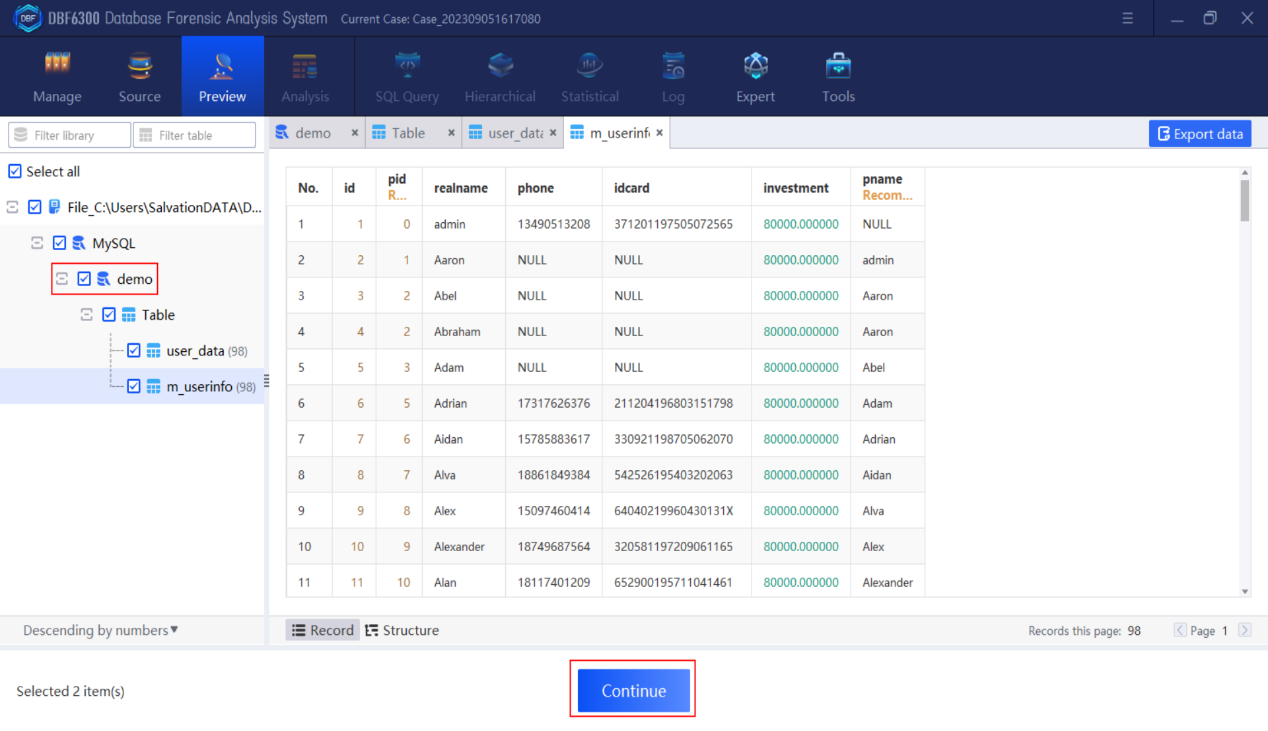
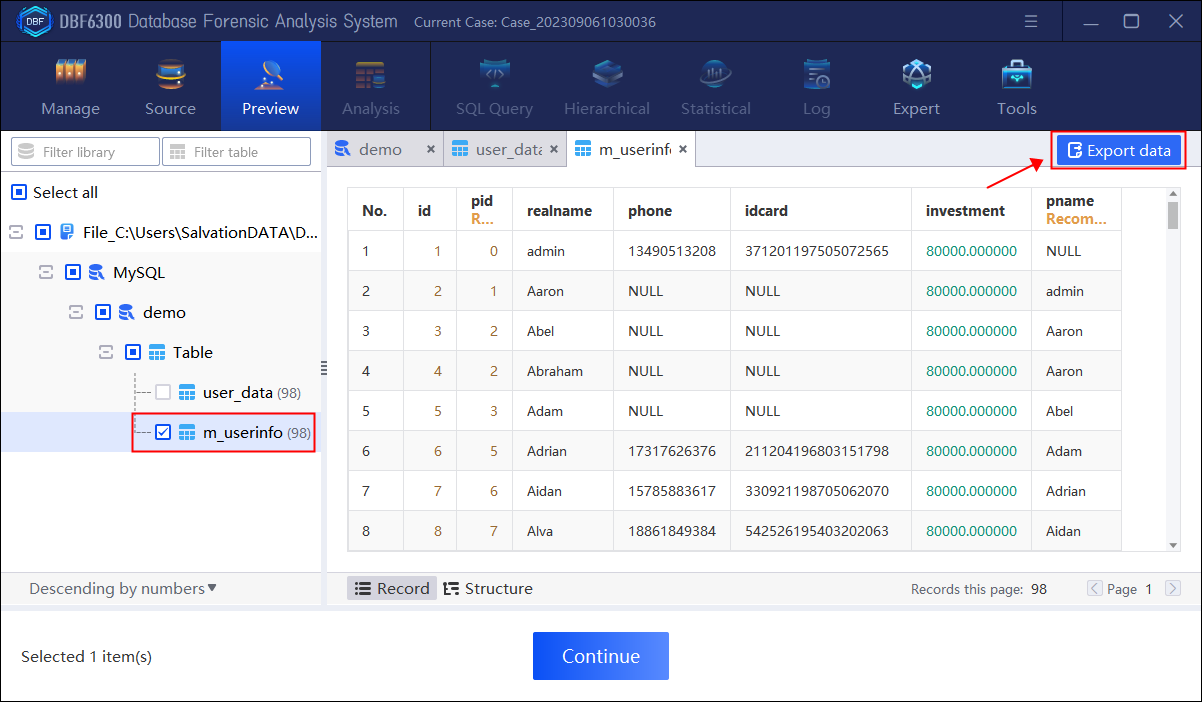
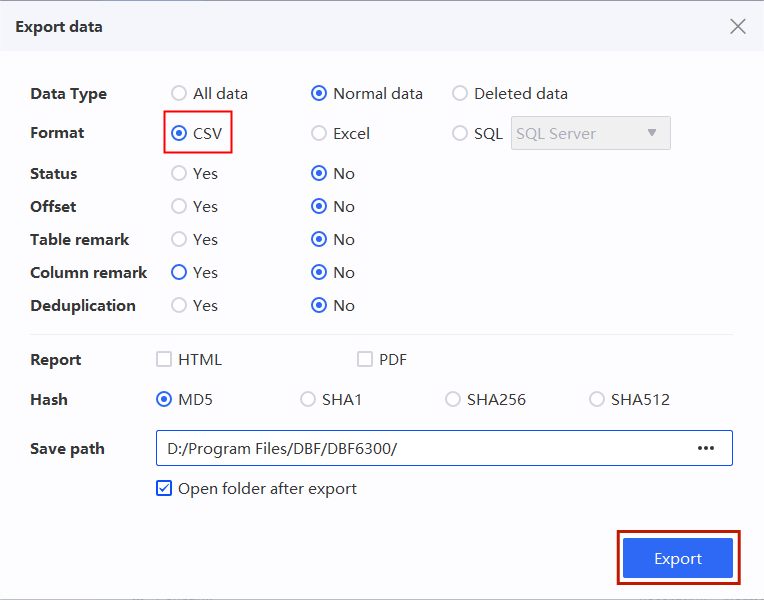
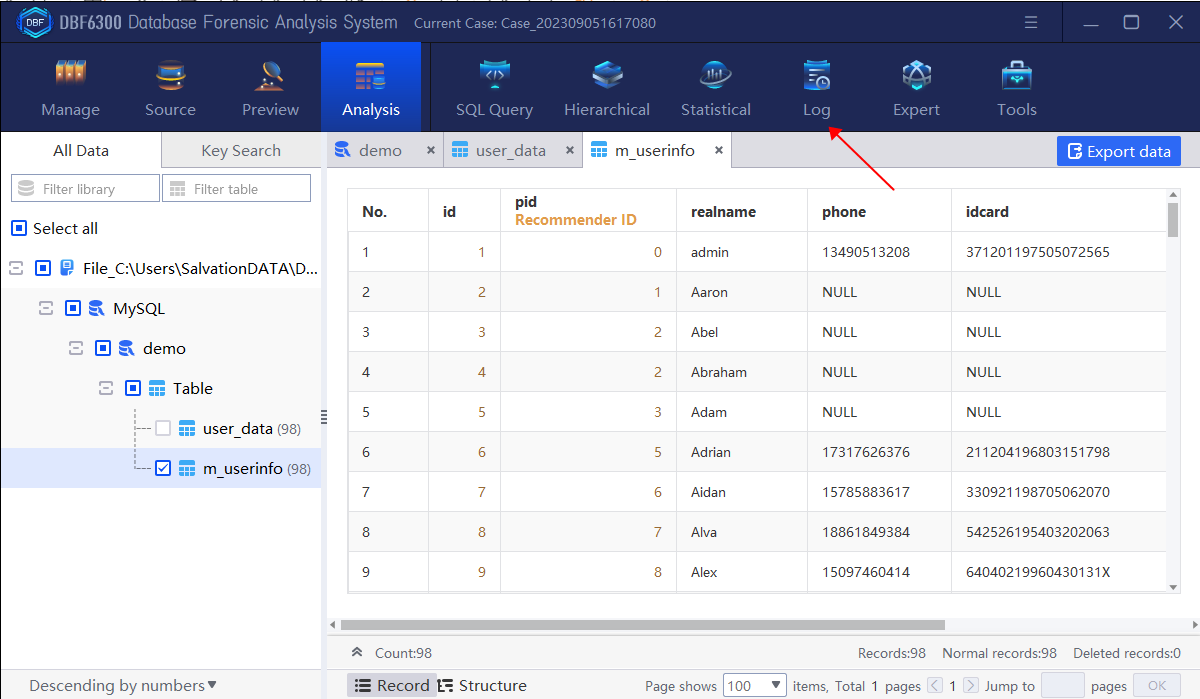
Step 3. Export the table which stores the information of the suspects involved in the case (including member ID, referrer ID, name, mobile phone number, certificate number, investment points, referrer username).
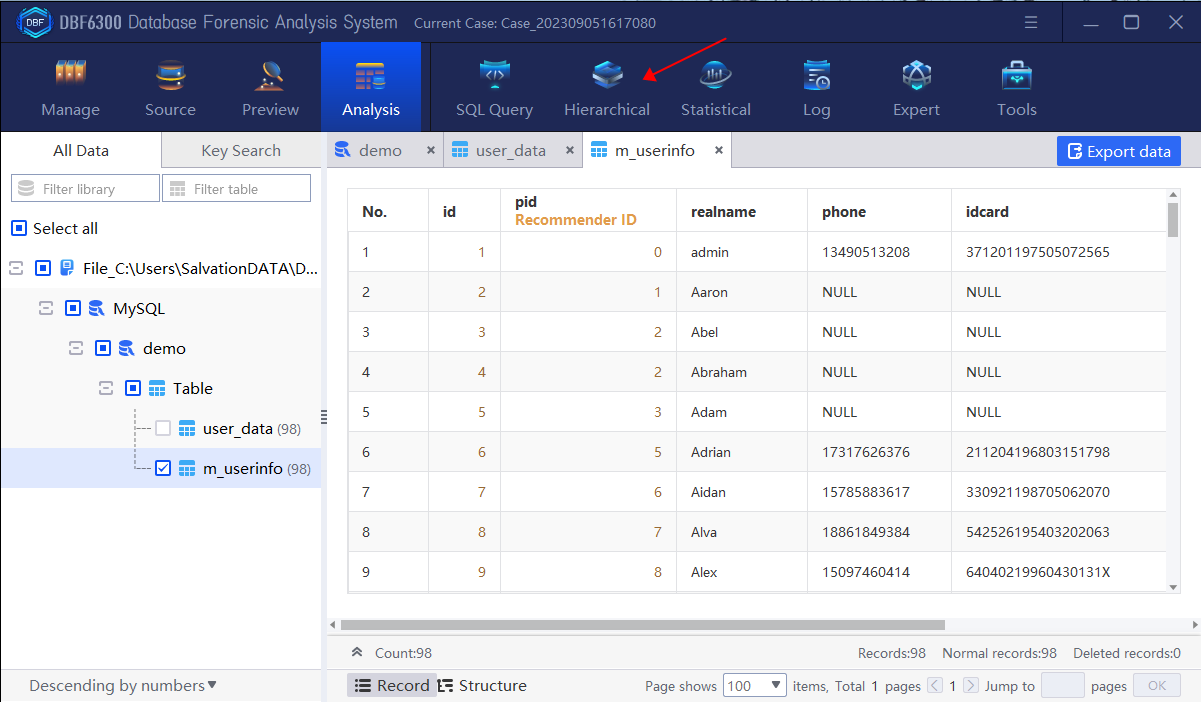
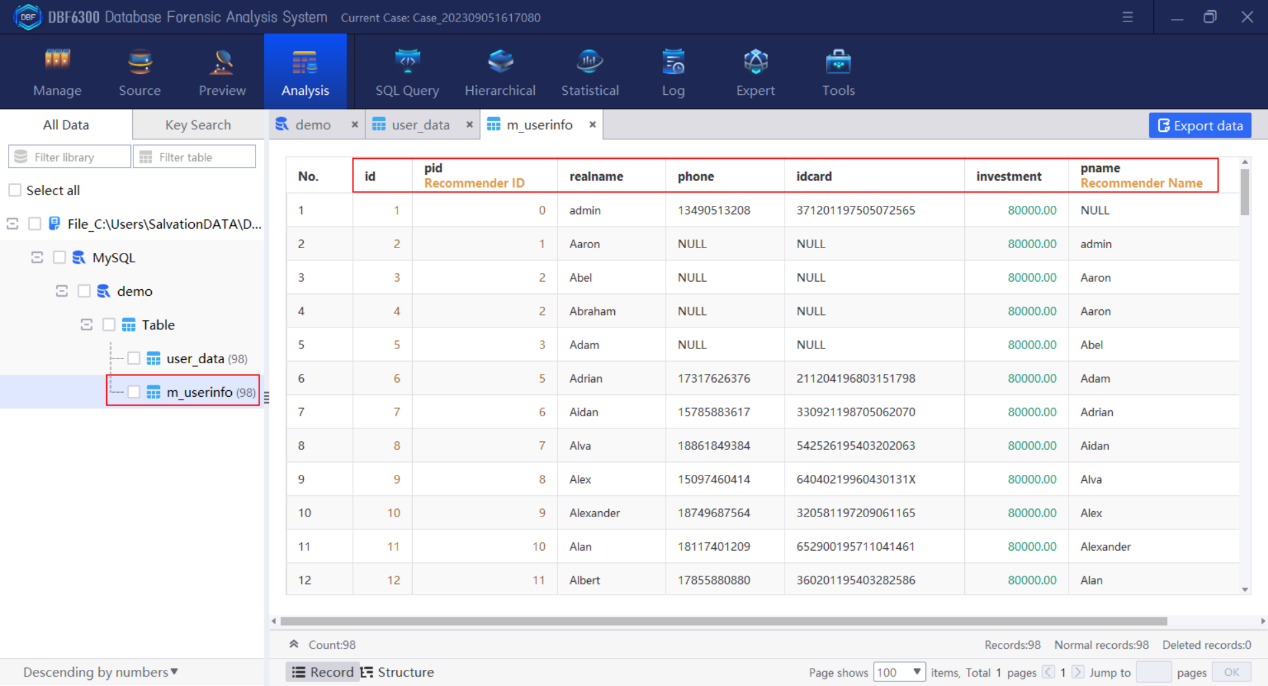
1.By checking the table information, find all field information contained in table “m_userinfo”.
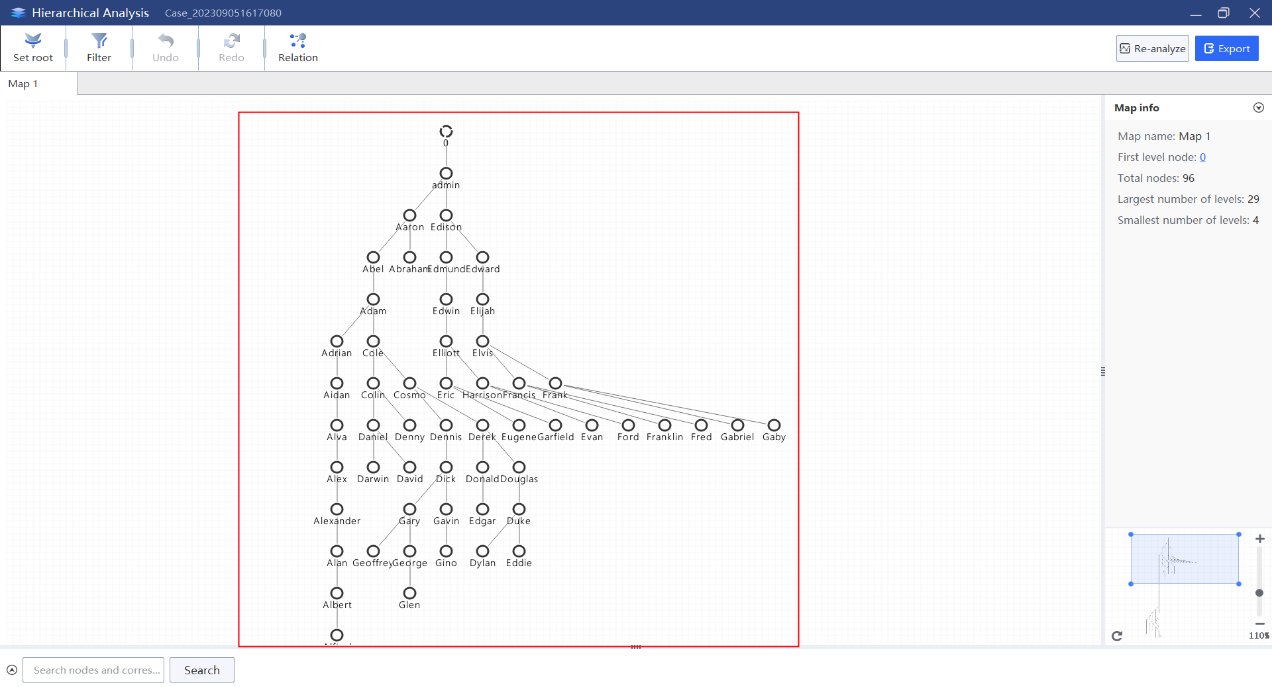
Step 4. Analyze the personnel organizational structure of the platform, and display the hierarchical map with username node.
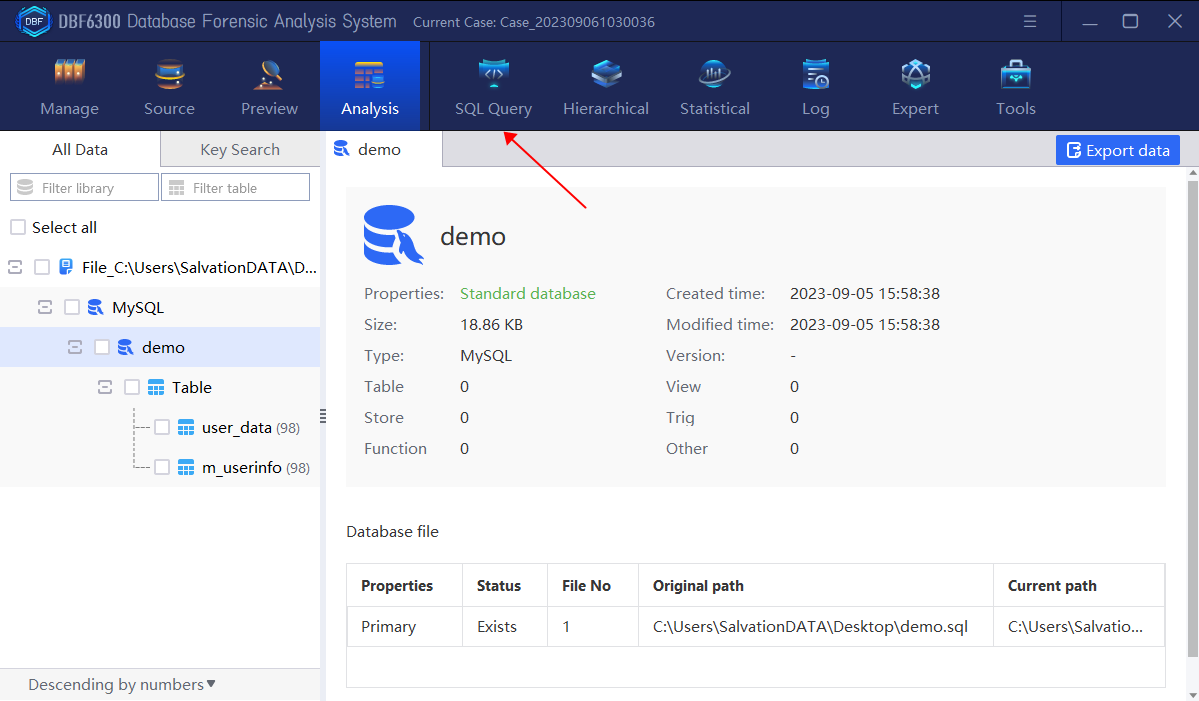
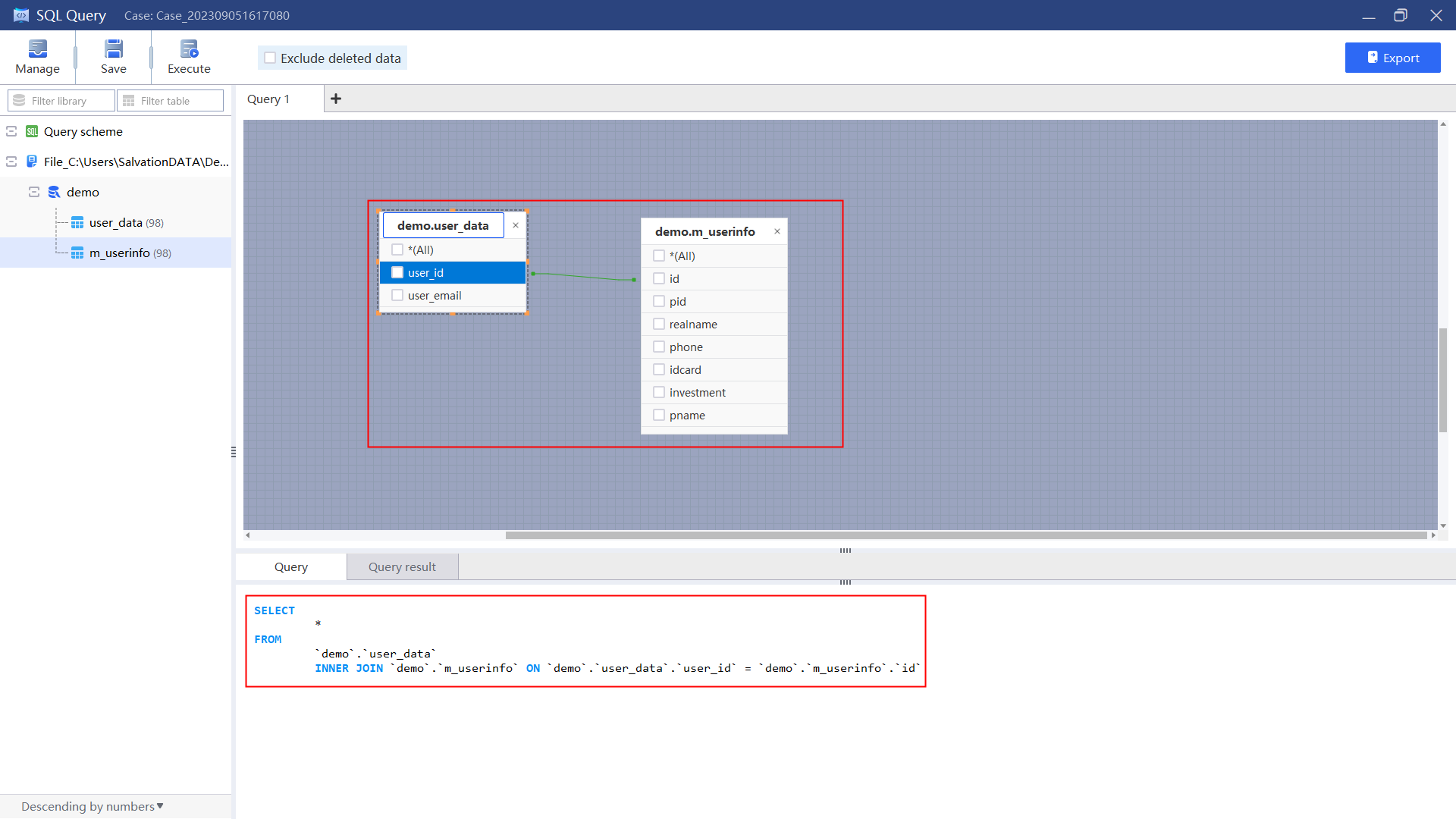
Firstly, we should analyze the table containing the superior-subordinate relationship field and user name field. Here we need to operate the relational query between the table “m_userinfo” and “m_userdata” to obtain the required table, and then perform hierarchical analysis according to the obtained table.
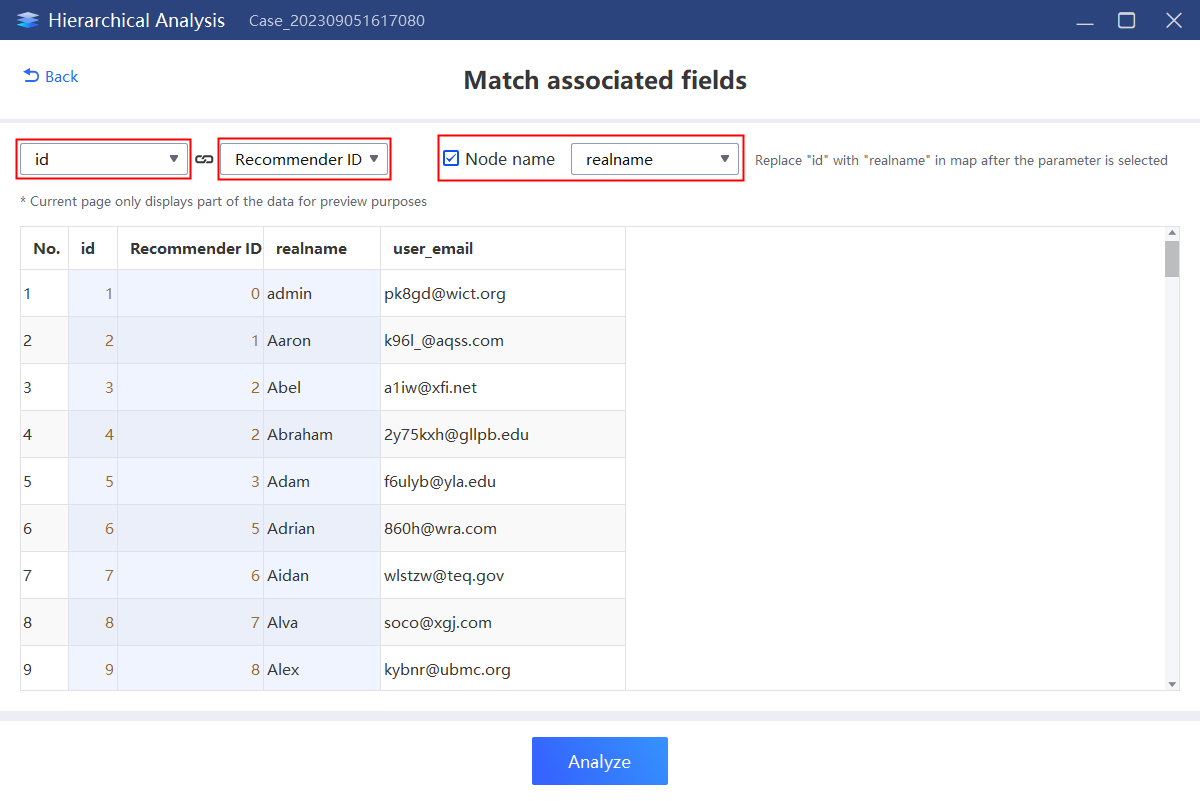
1.Select “SQL Query”, add table “m_userinfo”and “m_userdata”, select fields with the same meaning to associate.
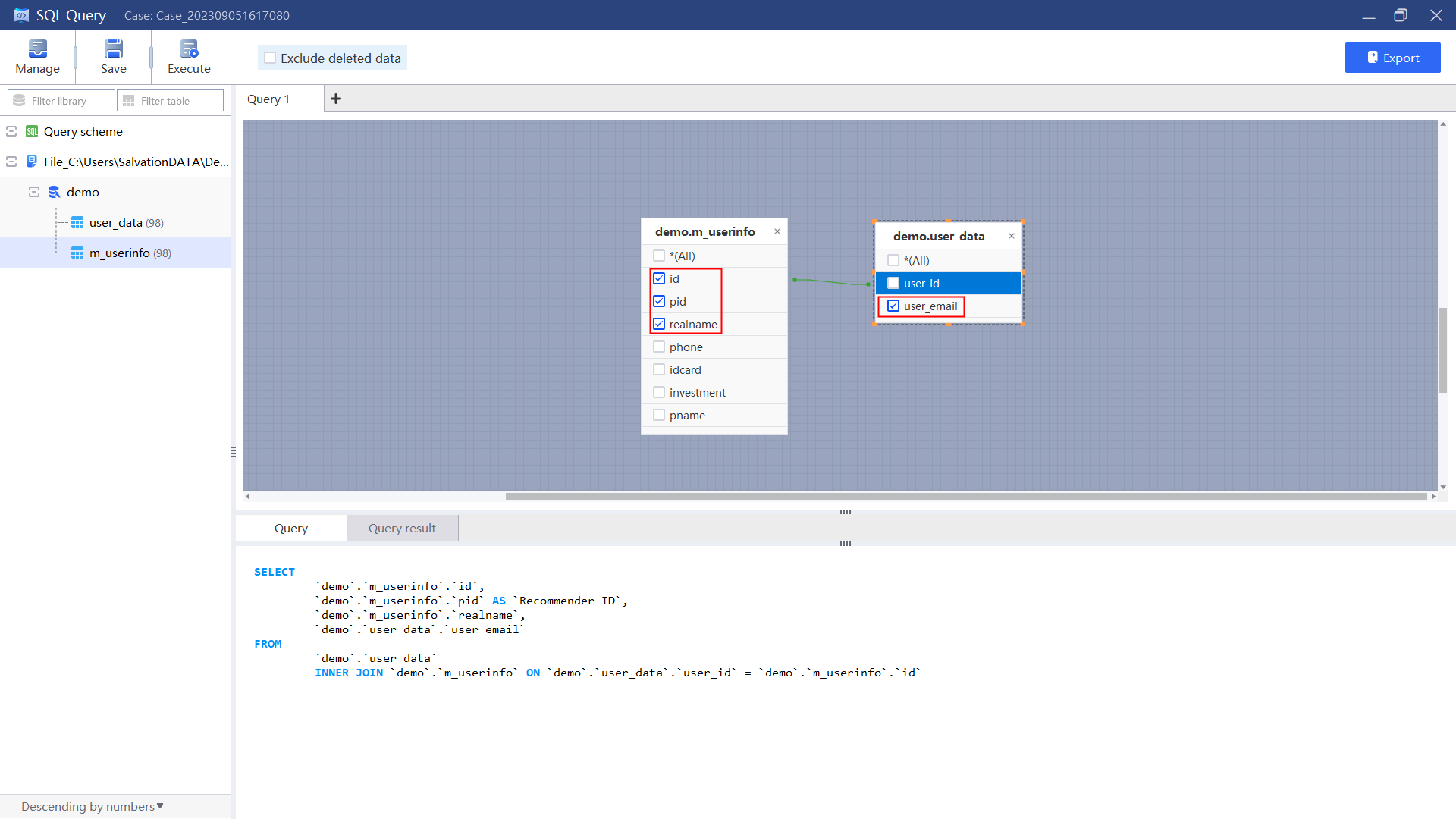
2.Select the fields to be included and execute the query.
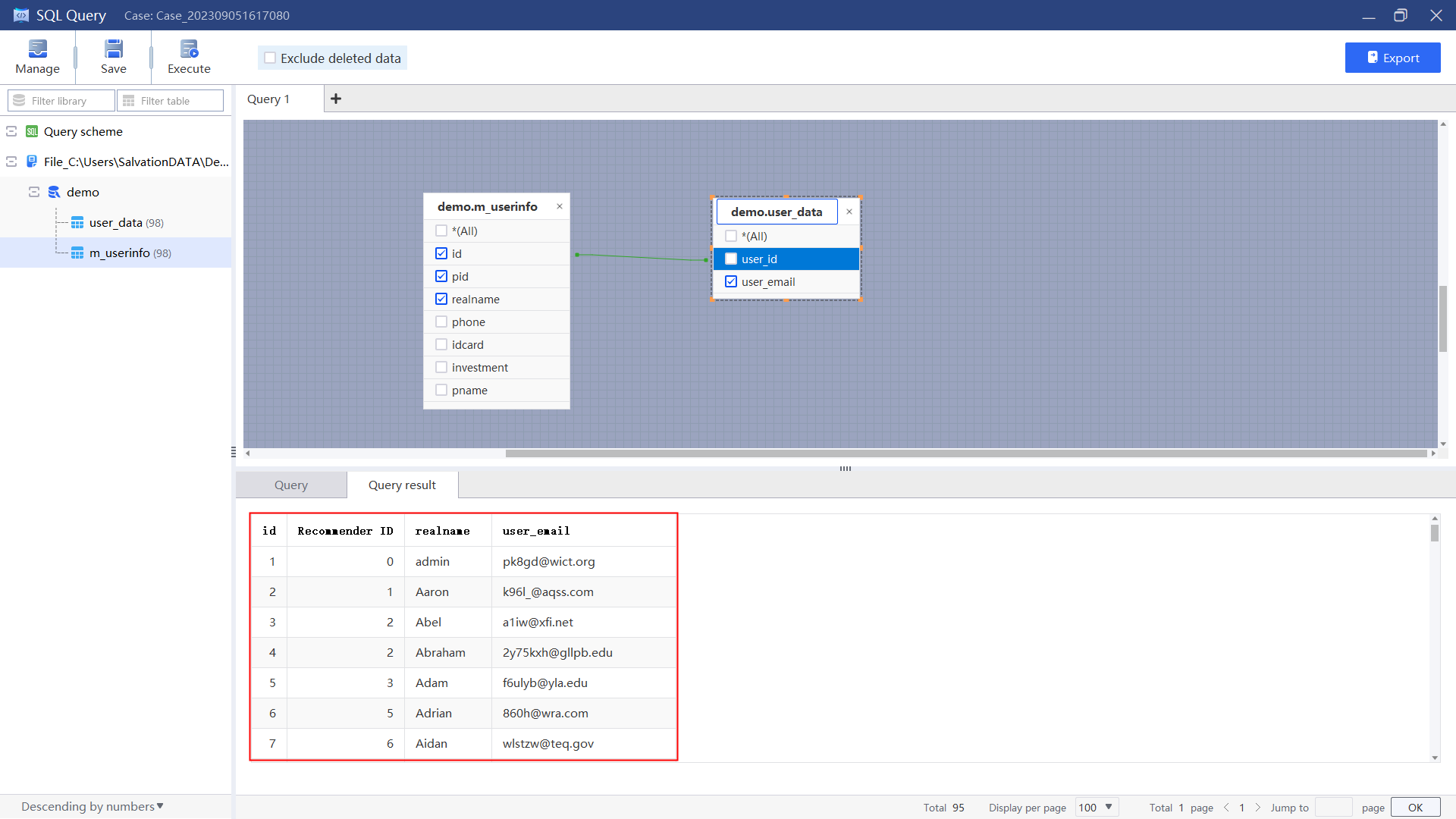
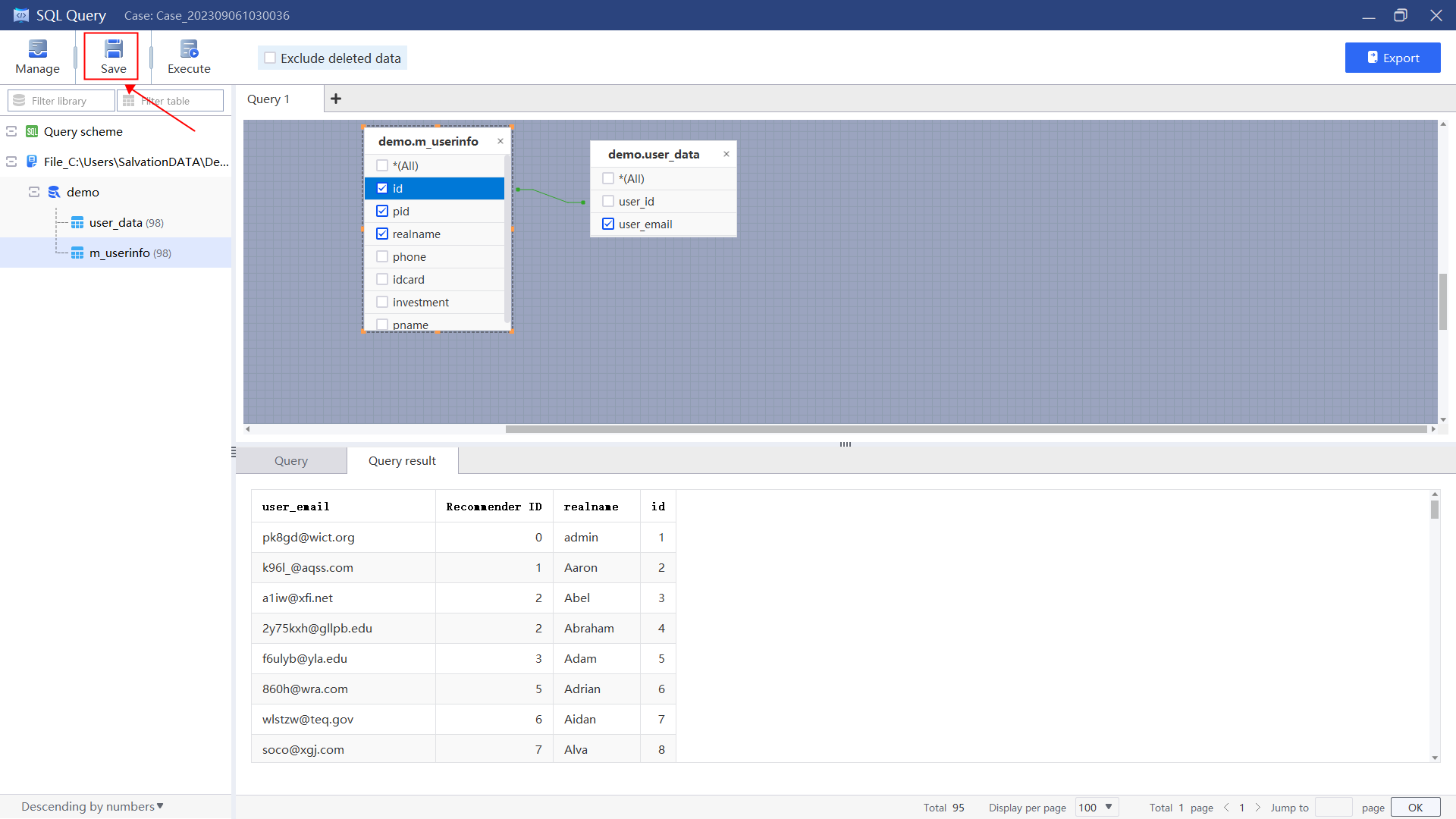
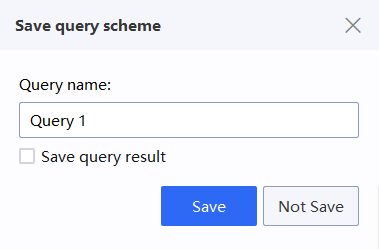
3.Save the query result for hierarchical analysis.
4.Select the “Hierarchical”, check the previously saved query result,and click “Next”.
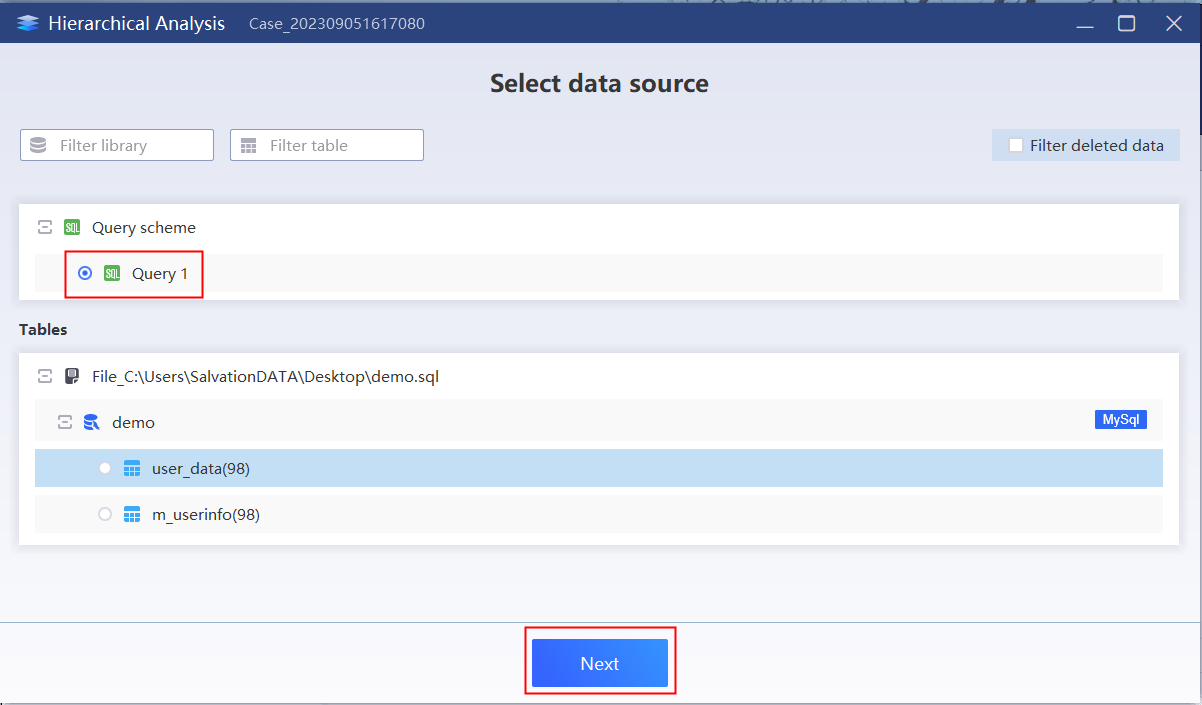
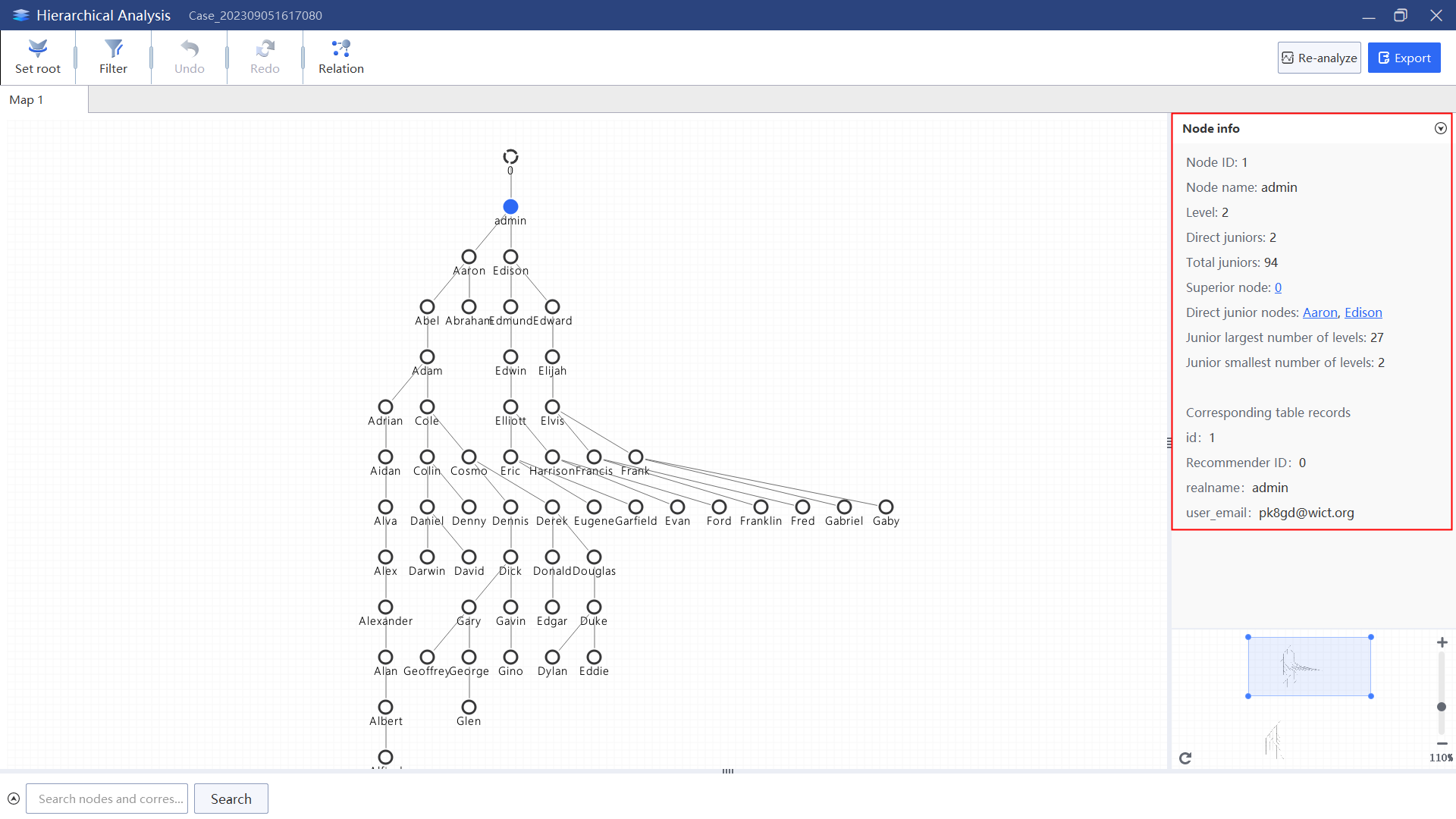
6.Through the database analysis map, the organization level and personnel size information can be obtained.
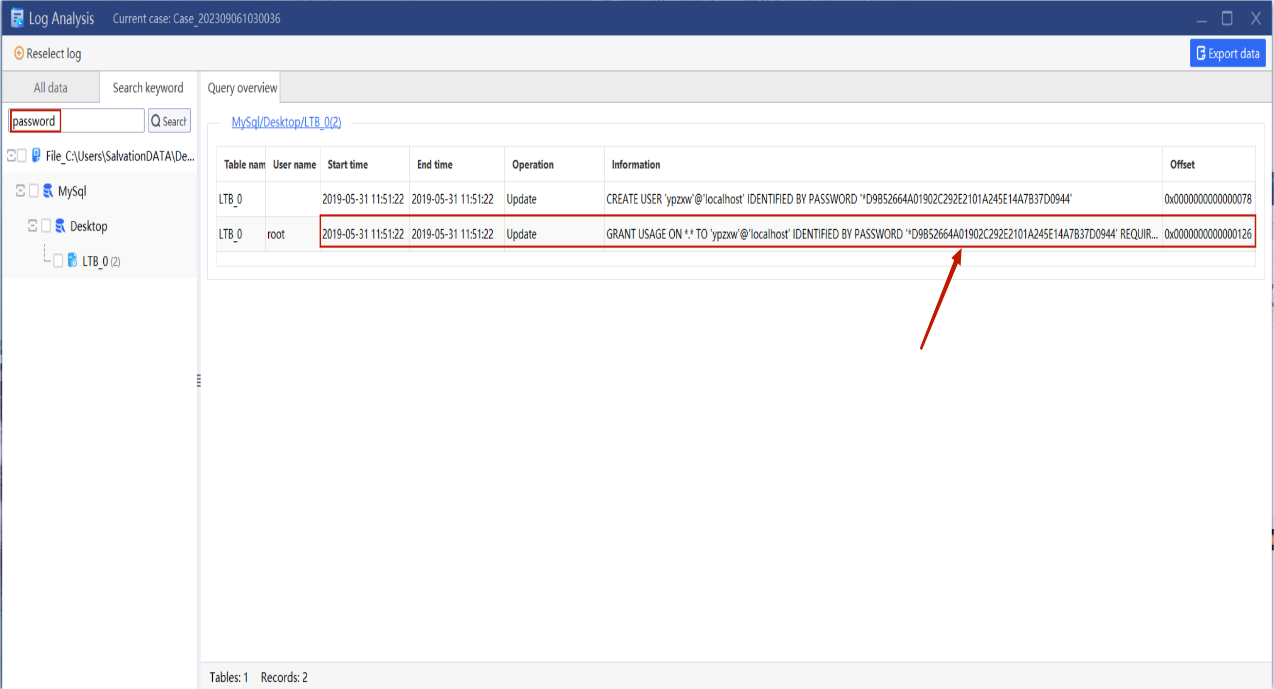
Step 5. Analyze the possible access password of the database
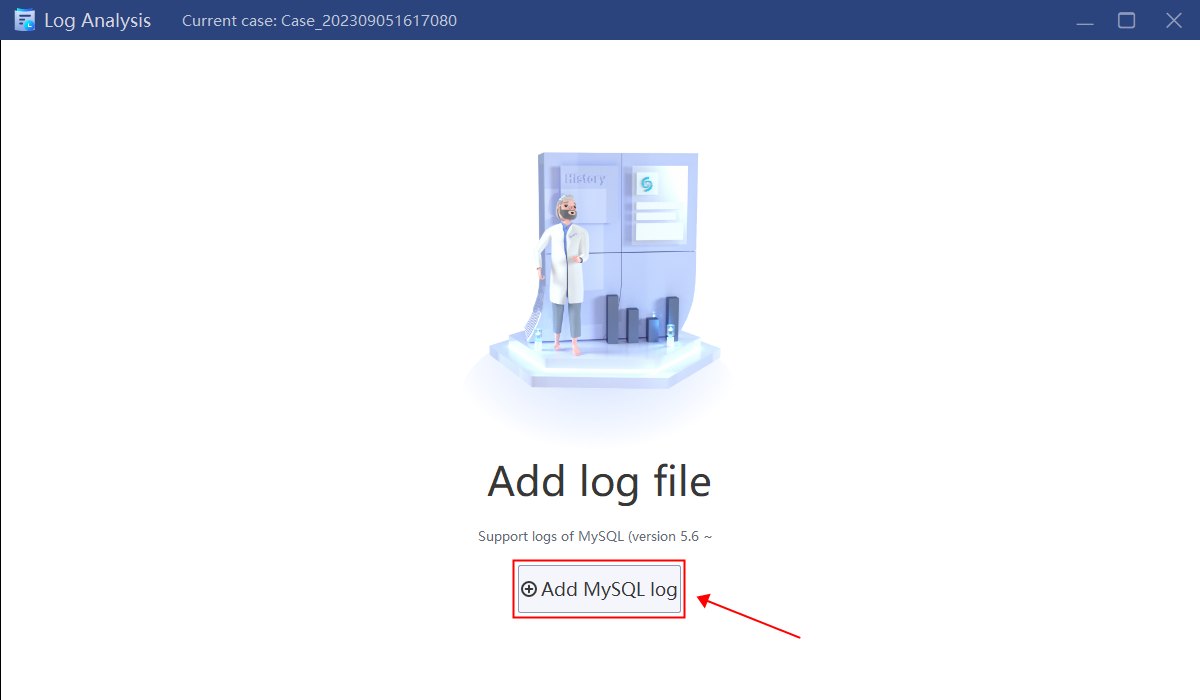
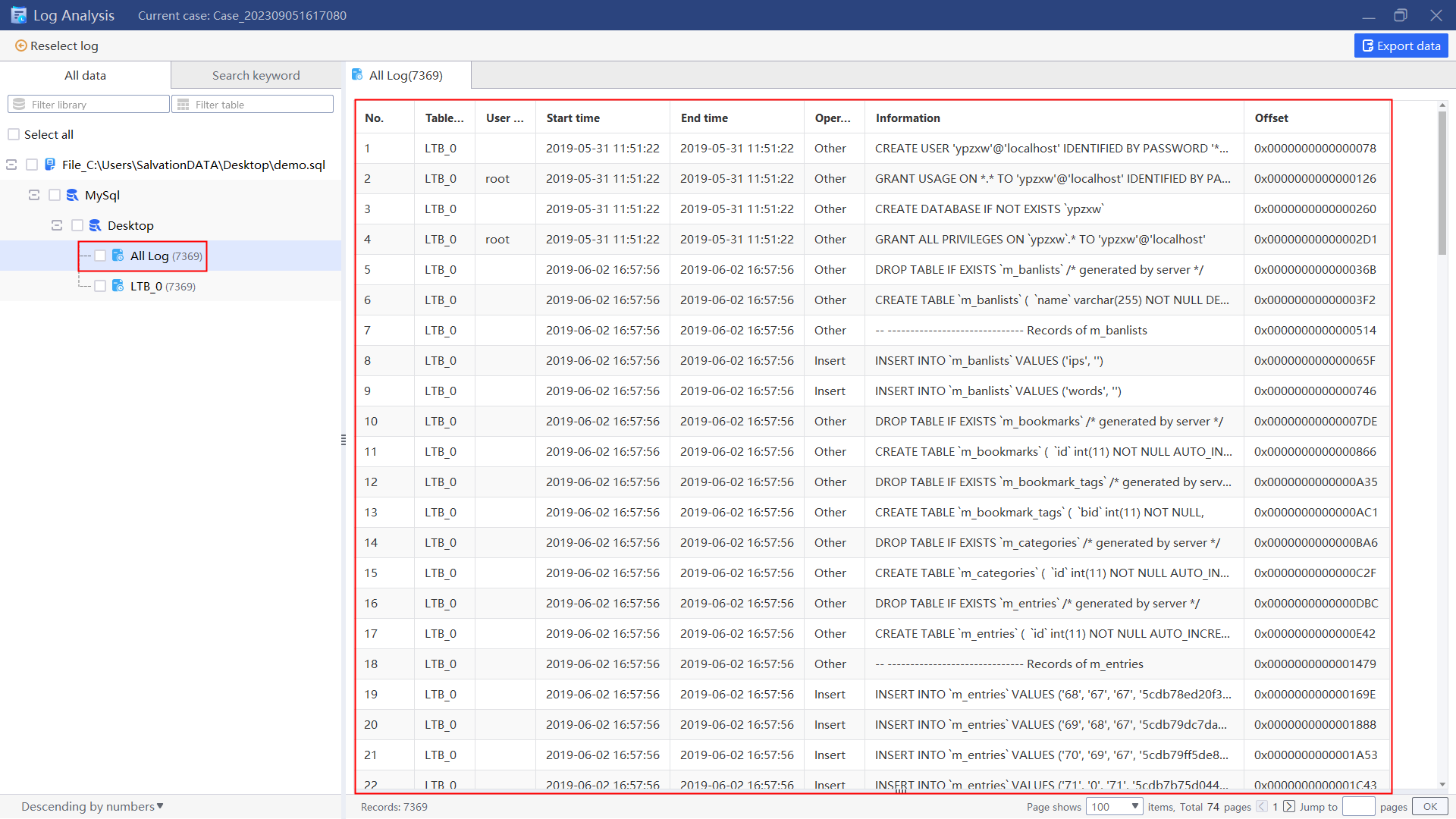
Add database log for analysis to check if there is a statement for setting a password, which can be achieved by using keyword “password” to query.
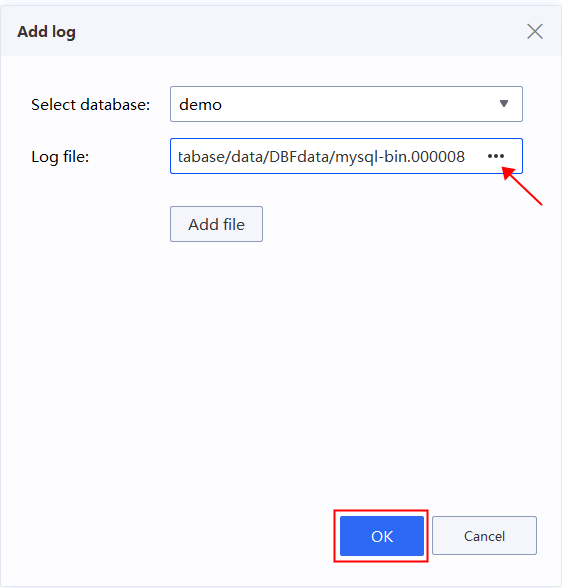
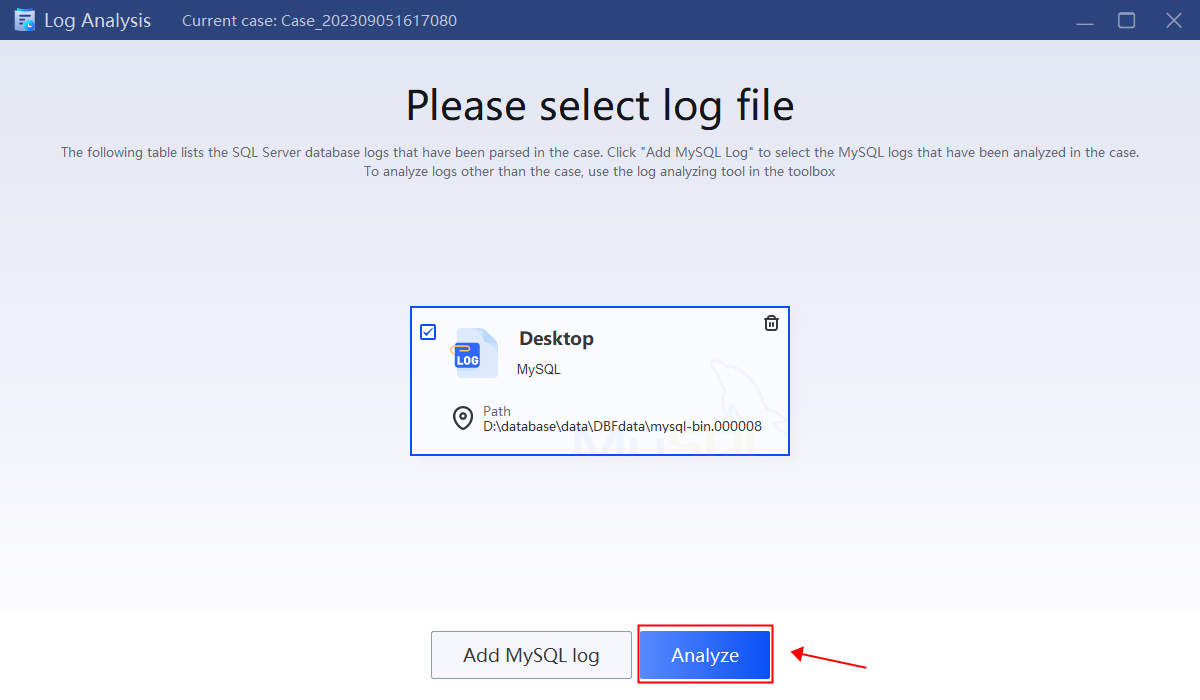
1.Return to the main interface, click “Log” and add log file of the database for current case.
2.Select the log file to analyze.
Notes
- Before conducting database analysis, it is necessary to clarify the meaning of the database, the tables and the fields.
- For log analysis, in addition to the logs recording additions, deletions, checks, and modifications in the case, there are also logs related to database access, management, etc., which also need to be analyzed when necessary.
- For cloud database backup files of some cloud platforms, due to their special format, format conversion may be required in advance.
- Database analysis is not limited to the database itself. Many cases also require local restoration of the database and network system.