How Database Forensics Works on New Cybercrime Platforms?

-
Content
- Intro
- What is the Database and What is Database Forensics?
- Why are Investigators Supposed to Use Database Forensics?
- Case Study
- How Does Database Forensics Work?
- Conclusion
-
Content
- Intro
- What is the Database and What is Database Forensics?
- Why are Investigators Supposed to Use Database Forensics?
- Case Study
- How Does Database Forensics Work?
- Conclusion
Intro
Nowadays, the number of new types of online crimes such as online pyramid schemes, online gambling, and online fraud has increased year by year, in which a large number of internet network platform models are used for dissemination and profit. For these cases, it is not only to use database forensics tools extracting, fixing, and recovering the public data and the background data, but also need to analyze databases that store the key clues including the personnel information and the financial information involved in the crime cases.
What is the Database and What is Database Forensics?
A database is where data is stored like your refrigerator to store food. We can also regard the database as a kind of investigative material equivalent to mobile phones and computers, and a warehouse for storing data, but the types of data they store are different. In mobile phones, the call records, the chat records of Telegram, Twitter, etc are mainly used as evidence or clues, while in the database, data has been stored as excel and records forms are stored to be presented as evidence or clues.
Database forensics is a branch of digital forensic science that focuses on the investigation and analysis of databases and their related metadata. It involves applying forensic techniques and methodologies to examine the contents of databases in order to gather evidence and uncover any unauthorized activities or potential wrongdoing. Just like computer forensics, the process of database forensics follows standard forensic procedures and involves the examination of both the database contents and the associated metadata.
Why are Investigators Supposed to Use Database Forensics?
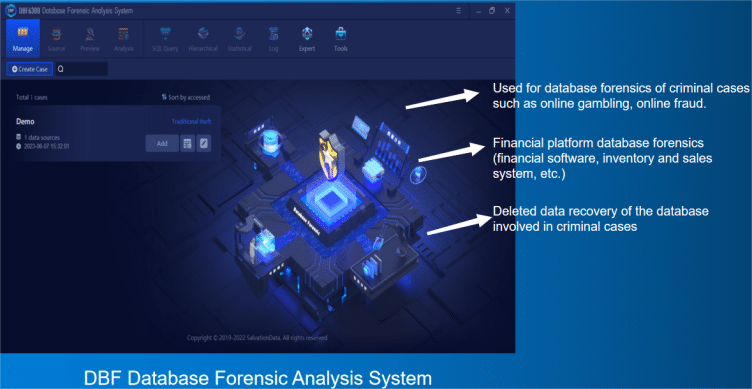
With the continuous increase of cybercrime, network forensics has become a major trend. In cases of online gambling, online pyramid schemes, and online fraud, most of the data involved in the case are stored in the database. In order to clearly analyze the criminal team’s organizational structure, capital outflow, personnel situation and other illegal information, it is necessary to use a professional database forensics tool and method to ensure the security of acquiring the data from various types of database.
Database forensics is actually to extract tables, records and other data involved in the databases related to the crimes which would be regarded as potential evidence and clues. The general workflow of database forensics is as follows:
Case Study
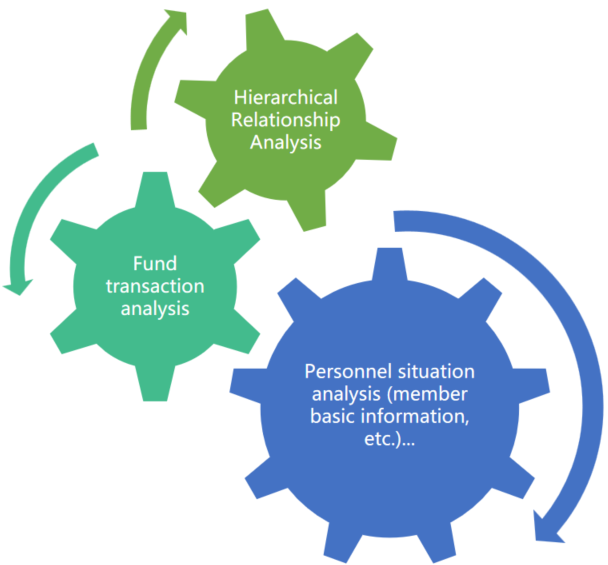
Take the online gambling platform as an example, gambling websites are divided into the front-end page and the database. The front-end page is the web-page where we can see or conduct betting transactions ourselves and the database is a data warehouse that stores relevant gambling personnel information, gambling cash flow information, and website information. For example, as for using the account password to log in to the website, trading, gambling and other relevant behaviors, the database can record our information and operations, generate tables of gamblers, trading funds, etc.
Through database forensics, we can acquire information such as the corresponding gambling personnel table and transaction fund table, which can help law enforcement officers to quickly sentence the criminals involved in the case with reference to the sentencing standards based on the obtained information and law of different countries.
How Does Database Forensics Work?
1. Local Server Database Forensics
1) Method
Seize and seal up the server or storage media where the database files are stored, or perform image of all storage media or partitions of the storage media where the database files are stored; in special cases, if you need to extract the database files on site, please refer to the introduction in the subsequent article;
2) Note
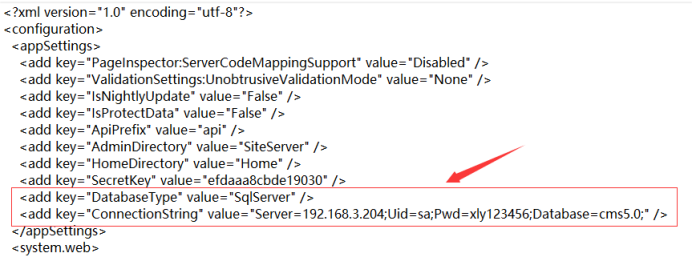
a) Investigators can confirm the database storage server through the database connection configuration in the network system.
The database connection configuration file is shown in the following chart(data type is SQL Server, which stored on the server with IP:192.168.3.204; database connected to the current website is named “CMS5.0”; database connection access account is “sa”, and the password is “xly123456”)
b) The hosts of the involved websites (and databases) in some local servers are virtual hosts;
c) The partition where the database file is located needs to be confirmed according to the specific database type and related configuration files;
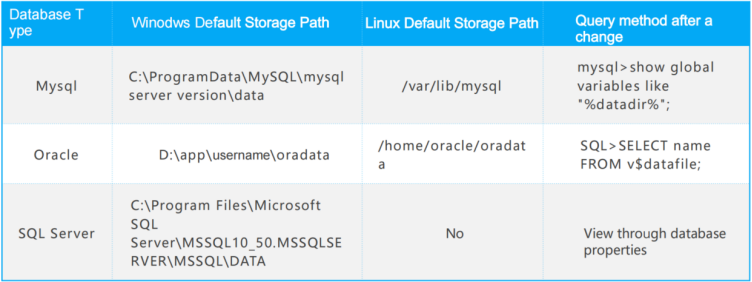
The default storage location and confirmation method of common database types database files, as shown in the figure.
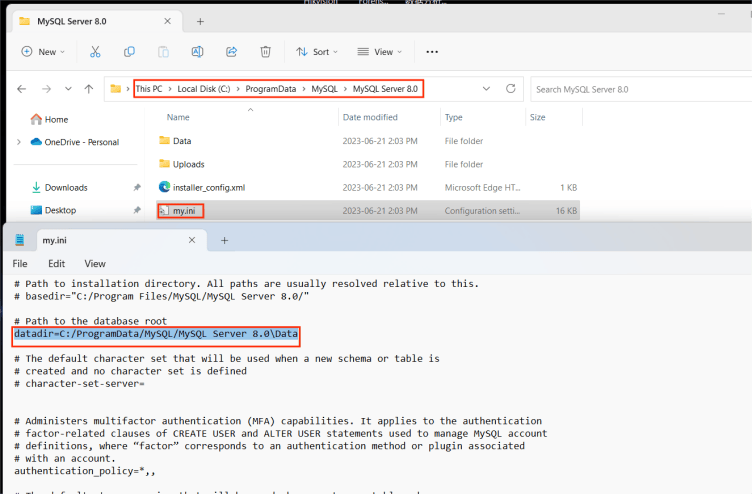
The database connection configuration file confirms the location of the database file, as shown in the figure is the storage location of the database file in the MYSQL database my.ini under Windows;
d) Investigators need to pay attention to the operational compliance when analyzing the local running database (memory data fixing, normal service shutdown and fixing, etc.), some databases will have post-simulation failures due to abnormal shutdown, and the specific situation will be discussed in detail;
e) When performing the imaging to the database files, be careful not to ignore to backup the related files, such as: SQL files, .bak files, Excel files and other formats of backup files;
2. Cloud Network Space Database Forensics
Cloud network space database forensic can be divided into various situations. Main purpose: fix the completed database files or perform the imaging to the whole space database files.
- Analyze the databases in the independent server host or virtual host
l Feature
With an independent operating system, leased the service of the communication operators. With public network or Intranet connection address and remote system management(remote desktop, SSH/xftp, service console, FTP management, DMS system, etc ).
l Method
| Method | Relevant Condition | Conditional access method |
| Communication
operator assistance |
Smooth communication process (domestic) | —— |
| Cloud Service console file download by WEB page
|
Acquire the login account and password of the console | -Enquiry system administrator
-Manage the Cookies in the computer’s browsers -Related records, etc. |
| FTP
remote download |
Acquire the login address, account number, and password of FTP | -Enquiry system administrator
-Manage the login history information of FTP in the computer -The related information of the communication operator service console -Related records, etc |
| Download by remote connection(Remote Desktop、SSH/xftp) | Acquire the address, account number, and password of the remote connection. | -Enquiry system administrator
-Manage the login history information of the remote connection in the computer -The related information of the communication operator service console -Related records, etc |
| Connect
database backup remotely (not recommended) |
Acquire the connection address, port, account and password of the database | -Enquiry system administrator
-Manage the login history information of connecting the database remotely or backup files in the computer -The related information of the communication operator service console -Related records of database connection configuration files in website files, etc. |
l Note
a) To keep the whole database files to ensure the max possibility and security of acquiring the complete database. Make it more favorable for data recovery and database log analysis when the data has been deleted.
b) Fix the complete database files involved in the case, mainly including database data storage files and log files.
c) It may be necessary to adopt the ways of social engineering, infiltration, inquiry by system administrators, and managing the relevant historical information.
d)For the cloud operator where the database with a smooth communication process (domestic) is located, it is recommended to assist in the investigation to make the data more complete; in view of the fact that the cloud data is easily destroyed remotely, the database fixing is completed according to the remote inspection standard on the premise of knowing the relevant remote connection information. Or seek the operator to freeze relevant data;
- Analyze the databases in the cloud space
l Feature
Only have permission to use related service on the host, leased the service of the communication operators. With public network or Intranet connection address and remote system management(remote desktop, SSH/xftp, service console, FTP management, DMS system, etc ).
l Method
FTP remote download, connect to database remotely to backup, the details are the same as before.
l Note
a) If the database is stored overseas, and only the original code file of the website is currently fixed, you can confirm the database connection information through the database connection configuration file in the code file (the connection information may be encrypted), and then remotely connect to the database for backup. However, the database obtained in this way only has normal data, and the deleted data cannot be restored;
b) For cloud space database forensics, it is recommended to use FTP remote download to obtain complete database files, and later extraction and analysis can get more useful information;
c)More attentions should be paid to the timeliness, and secure the certificate in time to prevent data from being destroyed;
Conclusion
Database forensics is a very important part of network forensics. To a network system, a database is like the relationship between a computer and a hard disk. A large amount of data generated by the network system involved in the case is stored in the database. Therefore, it is very important to complete database hardening in a reasonable and compliant manner. If you want to know more detailed steps, please contact SalvationDATA for consultation, or apply for trial use of relevant database security analysis products.