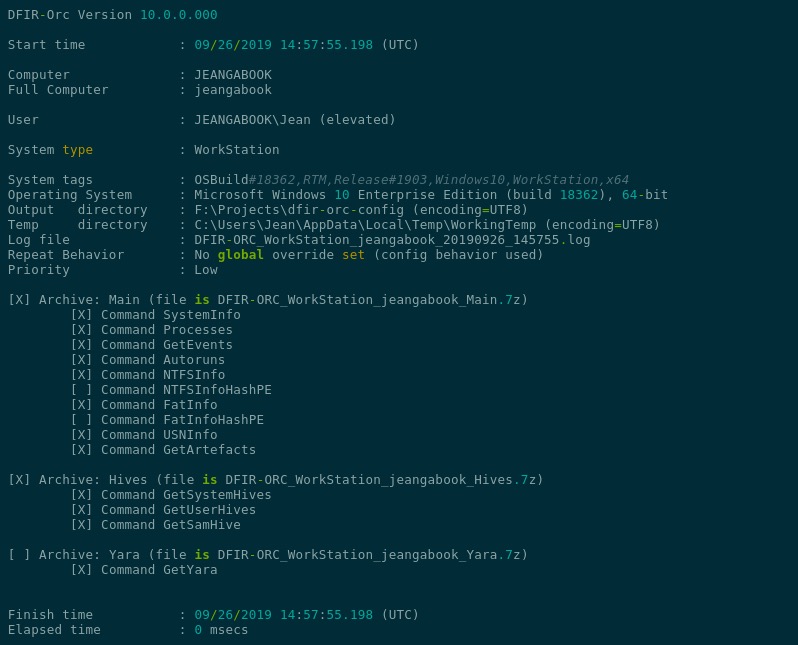
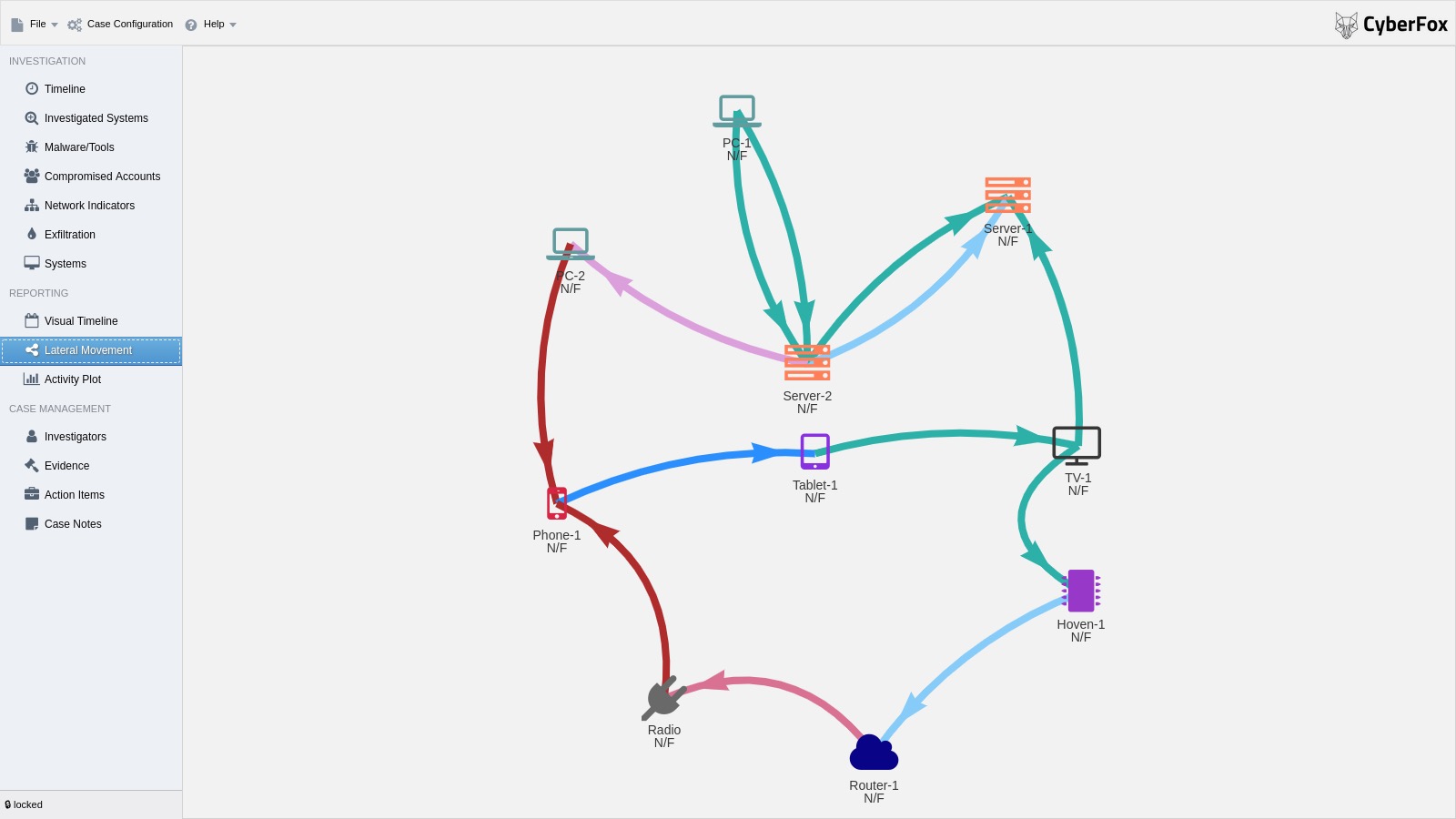
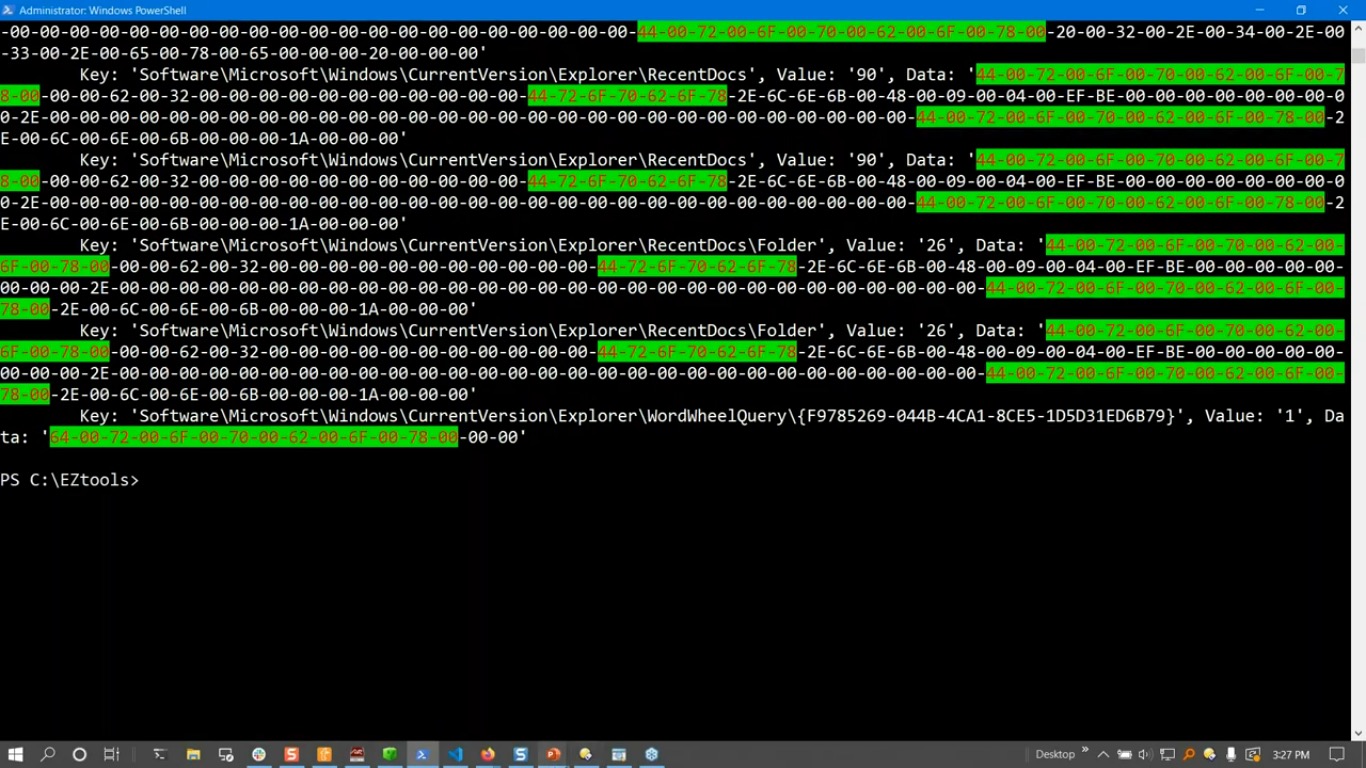
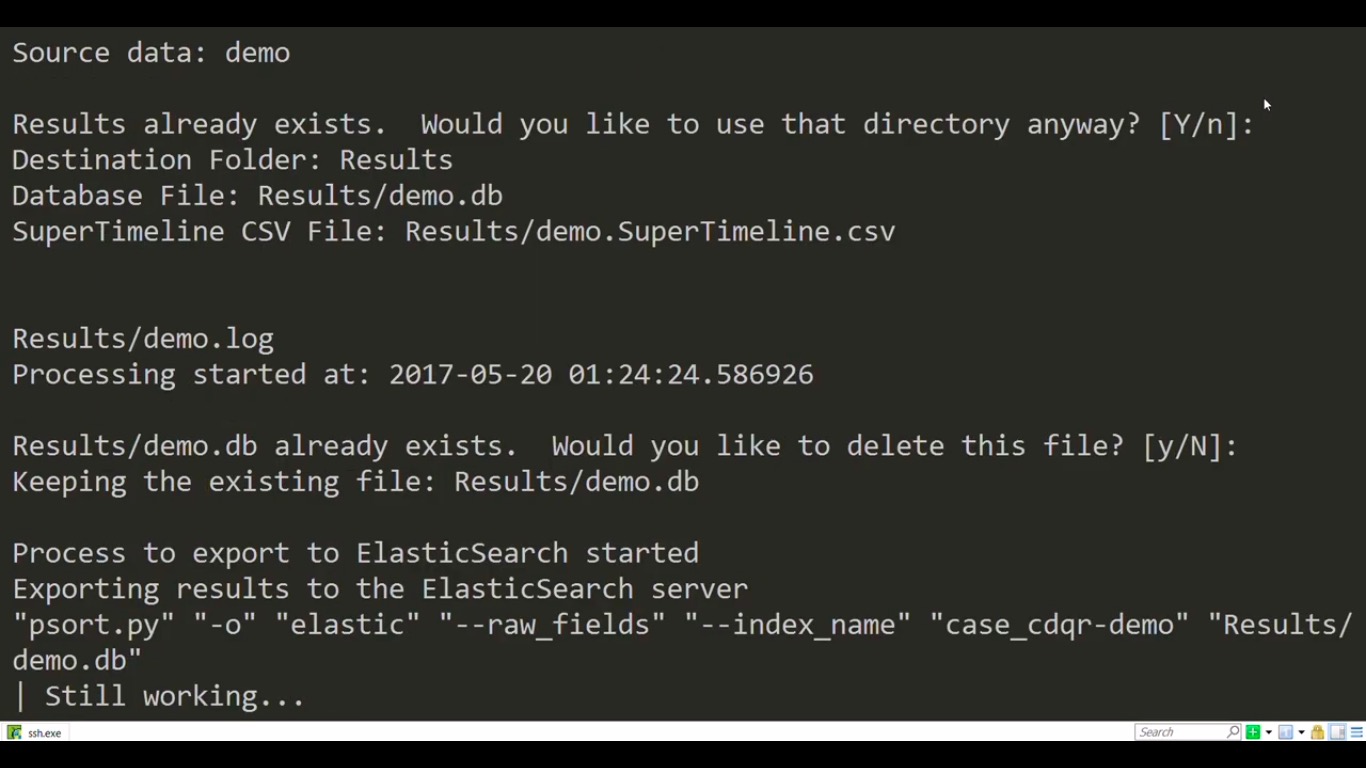
DFIR tools allow a qualified DFIR investigator to gather essential clues while preserving the business continuity with minimal disruption. The objective is to discover whether a breach has taken place, what are the circumstances surrounding it, who is behind it, and similar. Above all, the aim should be to salvage what can be saved and prevent a cyber security incident from becoming a full-blown cyber security disaster.
To avoid having to spend countless hours manually traversing the system and network architecture when searching for answers, these digital forensics tools will drastically speed up the process. Best of all, they come with an open source license, meaning they are free to use forever, even for commercial purposes.
In case you’d like to know more about the topic at hand, we suggest you read some of the previous articles we’ve published, including our introduction to DFIR and a more in-depth guide where we focus on the 6 phases of a cyber security incident response plan.
With that out of the way, here are the top 10 free DFIR tools you can use to increase the quality, speed, and accuracy of any cyber security incident investigation: